Table of Contents
Why B2B authentication is fundamentally different from B2C
Building authentication for a B2B SaaS product looks deceptively similar to B2C on the surface: users sign in, sessions are created, permissions are checked. But once you introduce organizations, admin hierarchies, enterprise IdPs, and security requirements, identity stops being a feature and becomes part of your application’s core architecture.
This post is a practical primer for developers who want to understand how B2B authentication works and how to build it without reinventing every wheel. We’ll walk through how B2B differs from B2C, the foundations of multi-tenancy, and the patterns you need for secure authentication and authorization. Along the way, we’ll highlight how Descope supports these use cases with native multi-tenancy, enterprise SSO, delegated administration widgets, and developer-friendly tools that keep your team from rebuilding the same infrastructure over and over.
If you’re building a product where companies, not individual users, are your customers, this guide is for you. You can also explore Gibber (our B2B sample application) to experience all the capabilities discussed in this guide and more.
Why B2B authentication is fundamentally different from B2C
B2C and B2B apps both deal with accounts, sessions, permissions, and authentication flows, but the similarities end there. Once you start selling to enterprises, the identity model shifts dramatically. Here are the core differences every engineering team should understand before building their B2B authentication stack.
Identity is organized around companies, not individuals
In B2C, users act on their own behalf. In B2B, users act on behalf of their organization, which becomes the primary unit of identity. That means:
Users must belong to one or more tenants (organizations).
Each tenant has its own policies, settings, and security requirements.
App access, roles, and permissions need to be scoped by tenant context.

Your backend must be able to answer “Which organization is this request for?” just as confidently as “Who is this user?”
Also Read: Multi-Tenant vs. Single-Tenant: Key Differences Explained
Enterprise SSO is expected from day one
Most consumer apps rely on email/password, social login, magic links, or OAuth with popular providers. B2B customers, on the other hand, expect to authenticate using their enterprise identity provider (Okta, Azure AD, Google Workspace, etc).
This also means your product must support:
Multiple IdPs across tenants
Multiple IdPs within the same tenant (common for large enterprises)
Easy, self-service configuration so admins aren’t filing support tickets to set up SSO
Enterprise SSO is often what enables a customer to roll out your product across their organization, and a dealbreaker if you can’t support it.
Access control is more complex
B2C apps typically rely on simple, global roles. B2B apps almost never can. Once organizations enter the picture, access control becomes deeply contextual and far more granular. Your system needs to support patterns such as:
Different roles for the same user across different tenants
Fine-grained permissions tied to specific resources or actions
Group-based access inherited from the customer’s IdP
Unlike B2C, where “admin vs. user” often covers most needs, B2B access control must adapt to each customer’s structure, and those structures vary widely across industries and company sizes.
Security, compliance & lifecycle management expectations are higher
Enterprise customers bring enterprise requirements:
Just-in-time provisioning (JIT) when a user logs in via SSO
SCIM for automated user provisioning and deprovisioning
Mandatory MFA enforcement
Strict audit logs for sign-ins, permission changes, and configuration updates
Automated user offboarding when employees leave the organization
B2B authentication and identity management has more moving parts and more risk, and requires careful coordination across users, roles, and policies.
B2B Enterprise Readiness Checklist
Score your tech stack on enterprise readiness pillars - from dev and IT experience to security and architecture.
Download
Multi-tenancy basics
When you serve multiple organizations from a single application, you’re operating in a multi-tenant environment. A multi-tenant architecture influences how you structure authentication, authorization, routing, data access, and even UI logic.
What is a Descope tenant?
A tenant in Descope is just any way of grouping users together, but in a B2B context, a tenant typically corresponds to one customer organization. Each tenant can have its own:
Users
Roles & Permissions
Authentication methods
Styling & branding
Your system needs a reliable way to map each authenticated request back to the correct tenant context. Without this, enforcing permissions or isolating data becomes impossible.
Descope’s tenant-first approach
A core challenge in B2B authentication and identity management is keeping a clean separation between who a user is and which organization they’re acting on behalf of. Many homegrown systems blur that line by trying to encode a user’s relationship to a company directly in their profile, which quickly breaks down when a user belongs to multiple organizations, needs different permissions in each, or interacts with shared resources.
Tenants as first-class objects
Descope avoids this problem by treating tenants and users as first-class objects with distinct lifecycles and responsibilities. A tenant represents a customer organization and carries its own configuration: everything from authentication settings and MFA requirements to branding, custom attributes, and session management.
A user, on the other hand, represents an individual identity that can participate in one or many tenants, with different roles and permissions in each. This model mirrors how real B2B SaaS platforms operate: people switch teams, contractors span accounts, and administrators often have broad privileges in one customer environment while having limited access in another.
By treating tenants as first-class citizens, Descope makes it natural to enforce boundaries between organizations. Each request includes tenant context, allowing your backend to reliably determine which customer’s resources the user is trying to access.
This tenant-first architecture unlocks a level of flexibility that’s difficult to achieve with improvised schemas. Instead of bolting organizational logic onto individual user records, Descope lets you model your B2B architecture directly: organizations with their own policies, users with multiple affiliations, and permissions that shift depending on which tenant the user is interacting with.
Flexible authentication methods per tenant
Tenants often have their own authentication requirements—one customer may enforce SSO-only login, another may require MFA, while a third uses passwordless flows for initial rollout. Every tenant can have its own mix of authentication methods, including:
SAML / OIDC SSO
Passwordless options (magic link, SMS / Email OTP)
Social login providers
Tenant-specific MFA requirements
If a tenant has SSO configured, Descope can automatically route users from that domain to the correct IdP. Until then, users can still authenticate through default login methods. This makes enterprise rollout smoother and reduces initial setup friction.
Also Read: Enforcing SSO for SSO-Enabled Domains
Self-service SSO and SCIM
Descope supports both SAML 2.0 and OAuth 2.0/OIDC specifications for single sign-on (SSO), allowing you to integrate with any identity provider (IdP) that implements either standard. In addition, our SSO Setup Suite is designed to provide B2B customers with the autonomy to configure and manage their SSO settings without external assistance.
The SSO Setup Suite walks your customers through the entire SSO configuration process, with templates for all common IdPs, and allows them to test the connection, minimizing any back and forth or setup errors.
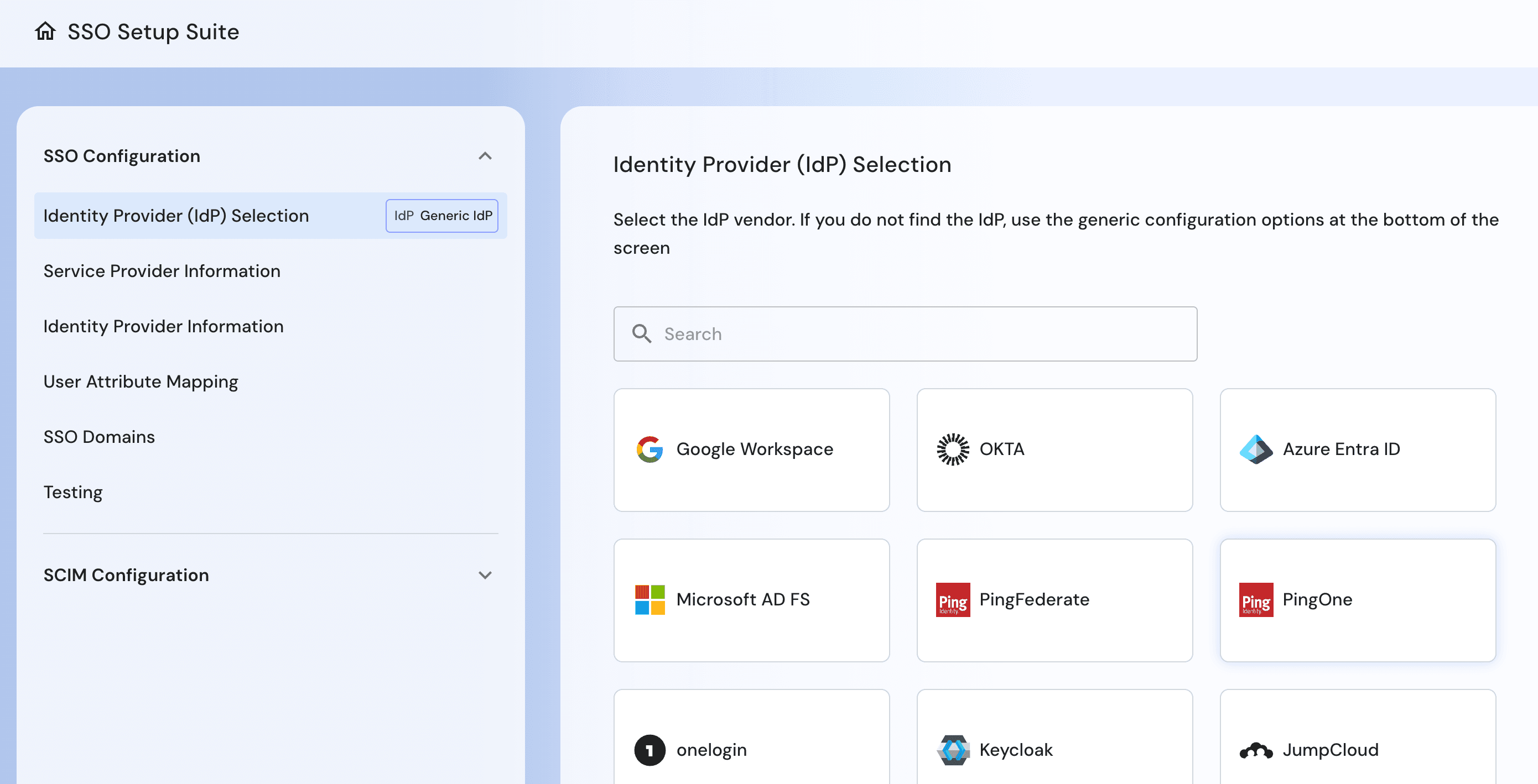
Descope also supports SCIM 2.0, enabling IdPs such as Okta, Azure, Ping Identity, and others to automatically provision, update, and deprovision users and groups in your Descope project.
Once SCIM provisioning is configured, updates made in the IdP (such as user creation, profile edits, group assignments, or deactivation) are automatically pushed to Descope. SCIM enables centralized identity lifecycle management and ensures that Descope remains consistent with your IdP's directory.
SCIM can also be configured directly by your Tenant Admins from within the SSO Setup Suite.
Tenant-aware authorization with roles, permissions, & group mapping
Once users are inside your product, B2B identity becomes an authorization problem: who can access what, within which tenant, under which permissions? Every customer expects your app to respect their org chart, their approval flows, and their internal roles, even though these structures vary wildly from company to company.
Descope helps you model this cleanly. Tenants act as security boundaries, users can have differentiated roles/permissions within those boundaries, and permissions can be enforced in your backend.
For customers using their own identity providers, Descope also supports group mapping during SSO. That means roles can be granted automatically based on groups in Okta, Azure AD, Google Workspace, or any other IdP. When an employee moves departments or leaves the company, the changes flow downstream instantly—your application stays in sync without requiring manual updates.
To enhance the RBAC framework, Descope also supports Fine-Grained Authorization (FGA) patterns including Relationship-Based Access Control (ReBAC) and Attribute-Based Access Control (ABAC) as part of its authorization capabilities. These approaches allow permissions to reflect real-world relationships (such as ownership of a resource, membership in a project, or attributes tied to compliance requirements) giving you the flexibility to evolve beyond static role mappings when your product demands it.
Delegated identity management widgets
Once you support multiple tenants, you also need a way for each organization to manage its own users, roles, and settings without involving your support or engineering teams. Most B2B products attempt to solve this with custom-built admin dashboards—pages that require ongoing maintenance, complex authorization checks, and constant updates as new features roll out. It’s an enormous amount of work, and it rarely becomes a differentiated part of the product.
Descope’s Delegated Management Widgets eliminate this burden by providing embeddable, tenant-aware admin experiences that drop directly into your application. These widgets give each customer the tools they need to manage their organization: inviting and removing users, assigning roles, rotating access keys, inspecting audit logs, or updating configuration. Because the widgets are tied to the authenticated tenant context, they automatically enforce organizational boundaries and prevent cross-tenant access without requiring you to write any custom logic.
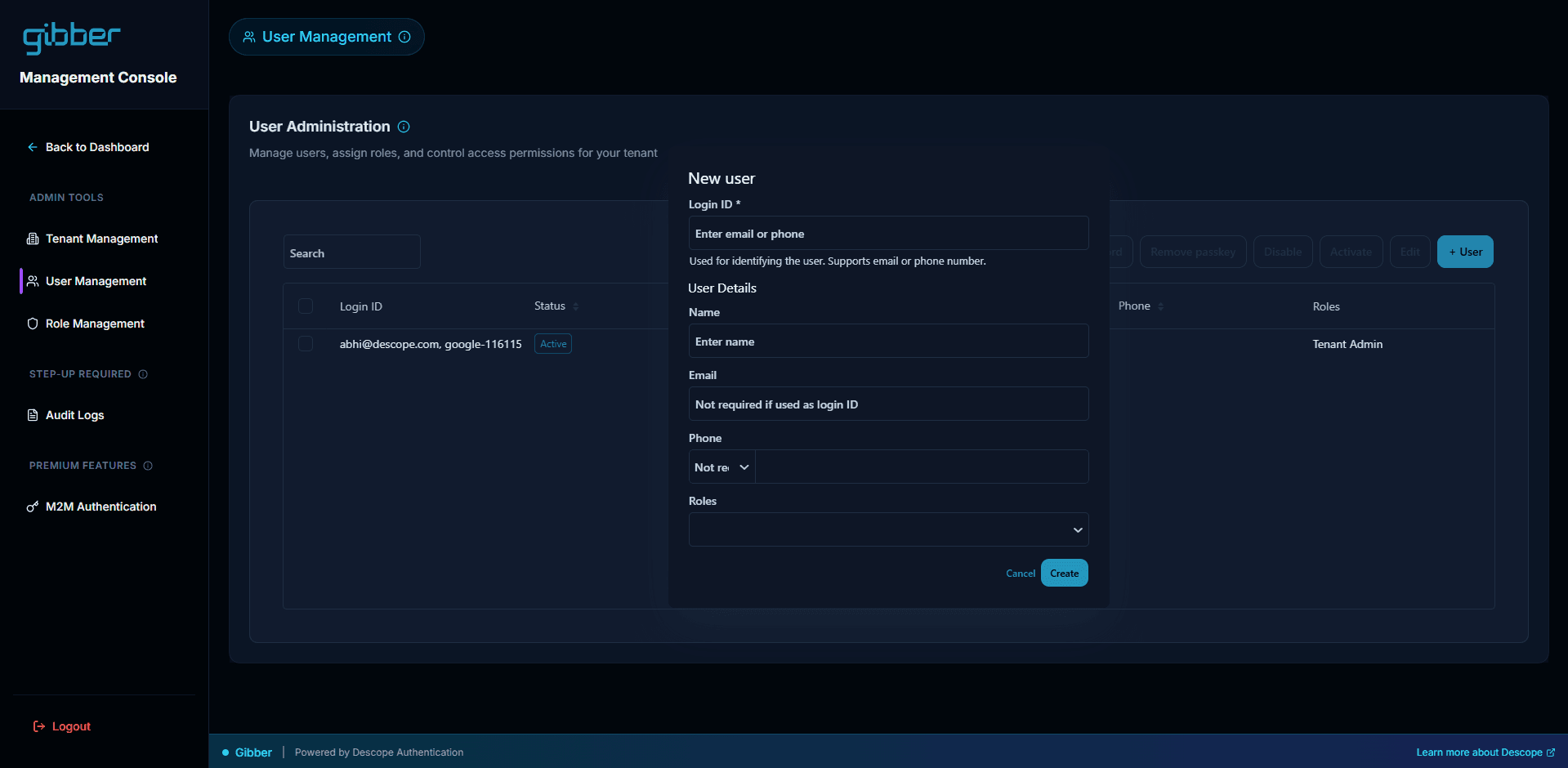
The result is a self-service management experience that scales with your customer base. New organizations can onboard themselves, administrators can control their own environments, and your engineering team can focus on product features—not rebuilding identity dashboards for the hundredth time.
Seamless B2B customer onboarding
B2B onboarding isn’t just about getting a user logged in—it’s about giving entire organizations a ready-to-use environment from day one. Descope provides the tools to make this process automatic, consistent, and tenant-aware, so new users and teams can start working immediately without manual intervention.
When a new user signs in, Descope can automatically detect their tenant based on their email domain, route them to the appropriate identity provider, and provision their account with the correct roles and permissions. You can even use connectors within your onboarding flow to sync with your CRM and automatically associate the user with the right account, team, or subscription plan.
Descope also handles the associated authentication and security flows seamlessly. MFA policies, passwordless logins, or SSO requirements are applied per tenant, so users only see the options relevant to their organization. At the same time, delegated management widgets allow tenant admins to configure SSO, invite users, and assign roles without ever needing your engineering team.
Drag & drop B2B authentication
B2B authentication isn’t just about letting users log in. It’s about building a scalable, secure, and predictable identity foundation that supports entire organizations. Multi-tenancy, tenant-aware authorization, and flexible authentication flows form the backbone of this foundation, ensuring that each customer’s policies, roles, and access rules are enforced consistently.
For developers, the takeaways are clear: treat tenants as first-class objects, enforce authorization within tenant boundaries, automate provisioning and onboarding wherever possible, and provide admins with self-service management capabilities. By doing so, you not only reduce operational overhead but also deliver the enterprise-ready experience that B2B customers expect.
With Descope’s no / low code capabilities for B2B SaaS authentication, you can implement these best practices quickly, securely, and at scale—letting your team focus on building product value instead of reinventing authentication infrastructure. Sign up for a Free Forever account today, and start delivering a seamless, secure, and scalable identity experience for your B2B customers.






