Table of Contents
Evaluation criteria: What makes a great CIAM platform
Customer Identity and Access Management (CIAM) has become one of the most important components of modern digital infrastructure, connecting security, compliance, and user experience across every application.
CIAM manages authentication, authorization, and privacy for external users such as customers, partners, or contractors. It ensures the right people (and systems) have the right level of access and that access is secure, efficient, and comes with minimal friction.
While workforce IAM focuses on internal employees, CIAM extends those principles outward to large-scale audiences where usability, consent, and scalability are just as critical as protection.
CIAM’s importance continues to grow due to major shifts in technology and regulation:
Passwordless and passkey adoption across consumer and enterprise apps.
AI agent and non-human identity use cases requiring machine-to-machine authentication.
B2B/B2B2X ecosystems with complex partner and tenant structures.
Privacy and compliance mandates under GDPR, DORA, NYDFS, and similar frameworks.
The right CIAM doesn’t just secure user access, but also improves conversion, retention, and trust.
Also read: IAM vs. CIAM Explained & How to Choose
Evaluation criteria: What makes a great CIAM platform
When comparing CIAM solutions, it’s not enough to look at login screens or MFA checkboxes. The strongest platforms combine security, usability, and developer efficiency in equal measure.
Key evaluation categories include:
Security & privacy: MFA, adaptive authentication, consent management, and compliance certifications.
User experience: Passwordless login, social sign-in, and customizable, omnichannel branded journeys.
Scalability: Ability to handle millions of identities and peak traffic seamlessly.
Developer experience: Comprehensive SDKs, APIs, visual workflow tools, documentation, and SDLC processes.
Integration ecosystem: Connectors for CRM, analytics, fraud, and AI systems.
Multi-tenant & B2B support: Built-in support for organizational hierarchies and partner identity.
Pricing transparency: Flexibility for startups and enterprises alike, with predictable cost structures.
With these criteria in mind, let’s look at the top 6 CIAM solutions today, each offering a distinct approach to balancing control, convenience, and scalability.
Descope
Overview
Descope offers a no / low code approach for organizations to build identity journeys for their customers, partners, AI agents, and MCP servers. Developers are able to use a visual workflow editor to create customizable flows for signup, login, MFA, SSO, consent management, and AI agent authentication–without maintaining servers and writing custom scripts, and without changing their existing identity stack if necessary. Ideal for B2C and B2B SaaS applications, as well as emerging scenarios like agent identity and MCP ecosystems, Descope excels where multi-tenancy, fine-grained access control, and delegated trust are essential.
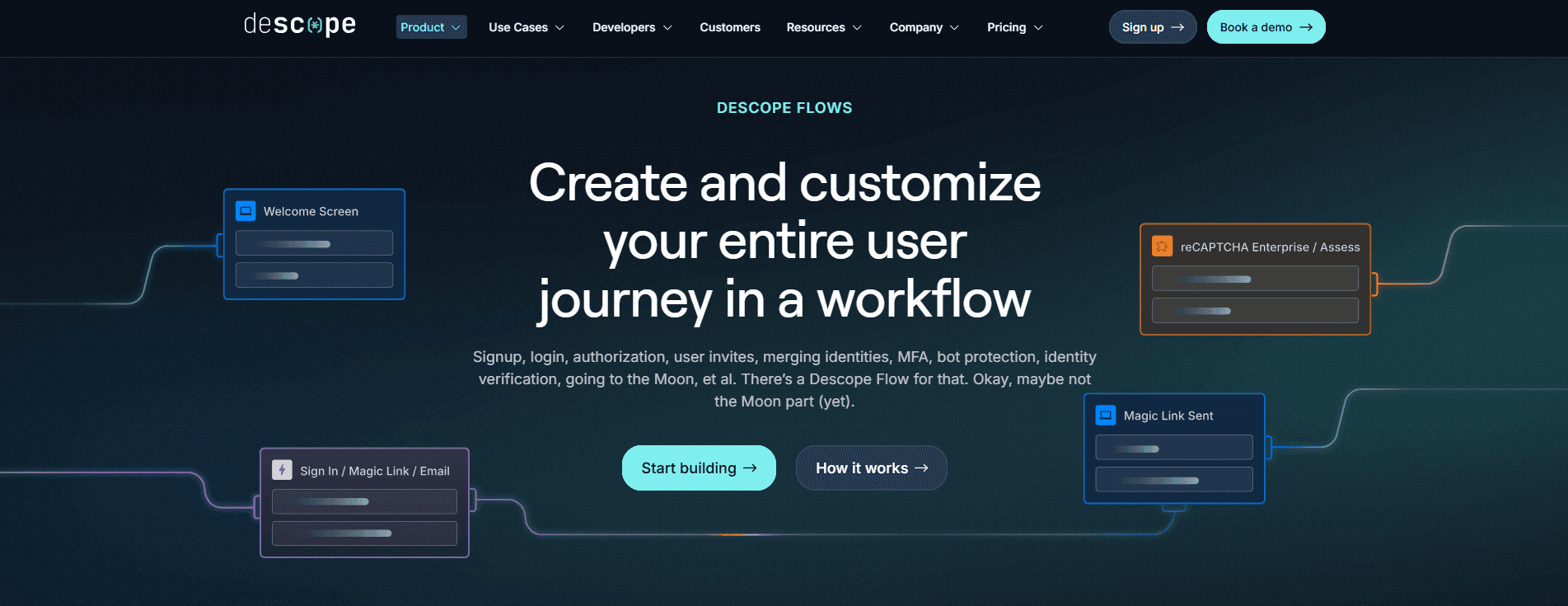
Providing a unified approach to authentication, MFA, SSO, and authorization, Descope supports both human users and AI agents natively, enabling teams to build secure, agent-ready applications without stitching together multiple identity components.
Key capabilities
Drag & drop visual editor to create and update login, signup, and MFA flows without code
Plug & play connector ecosystem for effortless integration with third-party services
Anonymous user tracking to improve top-of-funnel visibility for B2C use cases
SSO Setup Suite to configure, map, and test SSO and SCIM connections
Embeddable UI widgets that give users and admins self-service controls for managing access
Features a wide range of auth methods including passkeys, OTP, magic links,social login, and Google One Tap
Integrated multi-tenant management with RBAC and FGA controls
Extensive SDK coverage with 15+ SDKs for web, mobile, and backend environments, plus a full-featured REST API
Unified Identity orchestration that coordinates authentication, authorization, risk, and fraud tools
Agentic identity support to enable scoped, secure access for autonomous AI agents and apps.
Strengths
Visual workflow editor: Descope’s drag-and-drop builder allows developers to quickly design, test, and update login, signup, MFA, and SSO flows without writing code.
Transparent pricing and strong support: Descope offers straightforward, usage-based pricing with no hidden tiers or add-ons, backed by direct, responsive support and award-winning documentation. The platform has consistently earned the G2 Best Support badge for multiple quarters.
Simplified SSO management: Developers can configure enterprise SSO, SCIM provisioning, and tenant access through Descope’s visual workflows or user-friendly self-service portals.
Modern passwordless authentication: Native support for passkeys, magic links, OTP, and social logins makes it easy to eliminate passwords while enhancing both security and user experience.
Consistent omnichannel authentication: Authentication flows can be unified across web, mobile, and partner applications using the same no-code or low-code workflows, streamlining updates and scalability.
Built-in adaptive MFA: Adaptive MFA is included out of the box, allowing teams to apply step-up authentication dynamically based on real-time risk signals.
Enterprise agent ready: Descope supports secure authentication and access control for agentic AI systems using Inbound Apps, Outbound Apps, and MCP Auth SDKs.
Developer-first flexibility: Descope is built to adapt to any tech stack, giving developers the choice between hosted components or fully custom UIs. With extensive SDK and API support across React, Node.js, Python, Flutter, and more, teams can integrate authentication in the way that best fits their applications without being constrained by rigid frameworks or architectures.
Ideal for
SaaS platforms, marketplaces, and AI-driven products needing modern, extensible CIAM with low-code workflows and built-in multi-tenancy.
Auth0
Overview
Auth0, now part of Okta’s Customer Identity Cloud, has long been one of the leading CIAM platforms for developers looking to offload authentication and user management. It provides support for modern authentication standards (OIDC, OAuth2, SAML) and flexible APIs for integrating login, MFA, and SSO across web and mobile applications.
While Auth0 remains a leading option for large-scale identity deployments, teams often encounter tradeoffs around pricing, extensibility, and configuration complexity as projects grow. Still, for organizations needing enterprise-grade CIAM with strong compliance and global reliability, Auth0 continues to be a dominant force.
Key capabilities
Universal Login and Federation: Centralized, customizable login experience with support for social and enterprise identity providers using SAML, OAuth2, and OIDC.
Rules and Actions: Extend authentication logic with low-code scripts to enforce policies or trigger external workflows.
Adaptive MFA and anomaly detection: Built-in risk analysis and MFA enforcement to protect against suspicious logins.
SDK and API coverage: Most major languages and frameworks for building custom login experiences.
Strengths
Scalability: Auth0 supports millions of users and high-volume authentication workloads for global enterprises.
Ecosystem depth: Integrates with Okta’s governance tools and over 200 marketplace extensions for analytics, security, and CRM.
Customization flexibility: Developers can tailor user journeys through Rules, Actions, and APIs without managing backend infrastructure.
Ideal for
Enterprises and SaaS providers needing a mature, globally reliable CIAM solution with federation support and extensive customization options.
Amazon Cognito
Overview
Amazon Cognito is AWS’s managed service for authentication and user management. It automatically handles infrastructure, scaling, and availability, making it easier to manage identity at any scale. Cognito offers user pools for authentication, identity pools for temporary AWS credentials, and deep integration across the AWS ecosystem.
Key capabilities
Managed user pools for authentication, registration, and profile management
Built-in MFA and adaptive authentication to strengthen account security
SDKs for iOS, Android, JavaScript, and major backend frameworks
Native connections with AWS services such as API Gateway, Lambda, and IAM
Federation with social identity providers and enterprise IdPs using SAML or OIDC
Strengths
Fully managed service: Eliminates the need to host, patch, or upgrade your own identity infrastructure.
Strong security and compliance: Leverages AWS’s enterprise-grade security controls and certifications
Native AWS integration: Connects seamlessly with AWS tools for APIs, databases, and serverless applications
Automatic scalability: Handles millions of users without manual tuning or complex clustering.
Ideal for
Organizations building primarily within the AWS ecosystem that want a simple, scalable, and secure way to manage user authentication without the burden of maintaining their own identity stack.
Microsoft Entra External ID
Overview
A cloud-based identity and access management service, Microsoft Entra External ID is designed for organizations that need to securely manage and authenticate external users. Delivered as a fully managed service, it integrates deeply across the Microsoft ecosystem, combining authentication, lifecycle management, and governance in a unified platform.
Key capabilities
Enables branded and customizable user journeys for portals and applications
Provides lifecycle management features for provisioning, access reviews, and expiration policies
Includes built-in MFA, conditional access, and risk-based authentication
Integrates seamlessly with Azure AD, Microsoft 365, and other Microsoft cloud services
Strengths
Managed enterprise identity: Removes the need for self-hosting, maintenance, and scaling.
Governance and compliance focus: Includes native tools for auditing, access certification, and policy enforcement to meet enterprise requirements.
Deep Microsoft integration: Works natively across Azure, Microsoft 365, and related services for unified identity management.
Configurable user experience: Offers visual tools for designing and branding user journeys.
Ideal for
Organizations that operate primarily in the Microsoft ecosystem or want a managed identity solution with strong governance, compliance, and lifecycle management capabilities built in.
Keycloak
Overview
Developed by Red Hat, Keycloak is an open-source identity and access management platform. It delivers enterprise-grade authentication, authorization, and user federation across applications and services. Designed for flexibility, Keycloak gives organizations full control over login experiences, user management, and identity provider integrations, making it a strong choice for teams that prefer self-hosting and customization.
Key capabilities
Native support for SAML, OIDC, and LDAP protocols
Customizable login interfaces and authentication flows
Administrative console for managing users and roles
Self-hosted deployment with options for clustering and high availability
Strengths
Open-source control and flexibility: Keycloak is fully open source and free to use, enabling organizations to deploy and customize it within their own environment without licensing restrictions.
Enterprise protocol compatibility: Supports SAML 2.0, OpenID Connect, and LDAP natively, allowing integration with existing systems and diverse identity sources.
Customizable experience: Teams can tailor login pages, design user journeys, and implement custom authentication logic using Keycloak’s flow configurations and Service Provider Interfaces.
Ideal for
Organizations with dedicated DevOps resources that want a self-hosted identity platform offering complete control, transparency, and customization, and are prepared to manage its ongoing maintenance and updates.
Firebase Authentication
Overview
Firebase Authentication is Google’s managed authentication service within the Firebase platform, built for simplicity and speed. It provides a lightweight way to add secure login and user management to web and mobile apps. Designed for small teams and fast-moving projects, Firebase Auth integrates tightly with other Firebase services such as Firestore, Cloud Functions, and Firebase Hosting.
Key capabilities
Ready-made UI components for login and signup flows
SDKs for web, Android, iOS, and most popular frameworks
Support for email/password, social logins, phone authentication, and anonymous users
Native integration with Firebase products including Firestore and Cloud Functions
Strengths
Quick setup and easy integration: Developers can enable authentication methods directly in the Firebase console and connect them through client-side SDKs with minimal effort.
Mobile-first design: Optimized for Android, iOS, and cross-platform app development using Flutter or React Native.
Tight Firebase ecosystem integration: Works seamlessly with other Firebase tools, providing a unified backend experience for data, hosting, and serverless logic.
Ideal for
Startups and mobile-first teams looking for a fast, low-maintenance authentication solution that plugs easily into Firebase’s broader development ecosystem.
Conclusion
CIAM has become the backbone of digital trust, but not every platform strikes the right balance between security, scalability, and developer experience. Many teams start with established identity providers for reliability or compliance, only to encounter challenges around cost, customization, or multi-tenant complexity as their products grow. The best CIAM platforms today go beyond basic login to deliver flexible orchestration, passwordless access, and seamless partner and customer identity management.
Among the available options, Descope stands out for its developer-friendly visual workflows, built-in multi-tenancy, and support for modern authentication methods like passkeys, SSO, and adaptive MFA. By removing the friction of custom infrastructure and manual configuration, Descope helps teams launch faster, scale securely, and extend identity to users, partners, and even AI agents, all without writing code.
For more detailed information on Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account and start dragging & dropping your auth today!






