Table of Contents
What is user authentication?
User authentication is the entry point to every modern application. It secures accounts, protects sensitive data, and shapes the user experience while helping organizations meet compliance requirements. Without it, trust and safety quickly erode.
From consumer apps to enterprise SaaS platforms, authentication is a core foundation. The right approach can streamline onboarding, reduce abandonment, and defend against account takeovers, all while supporting growth and scalability.
In this blog, our focus will be on external user authentication. We'll highlight leading solutions in the market, outline their key capabilities, and explain which types of organizations can benefit most from each.
What is user authentication?
User authentication is the process of confirming who a user is before allowing them access to an application or resource. It is the foundation of digital security, helping organizations protect sensitive data, prevent fraud, and maintain trusted interactions with their users. Modern authentication spans multiple components that work together to balance security and usability:
Login methods: Traditional passwords as well as passwordless options like passkeys, magic links, and social logins
Multi-factor authentication (MFA): Additional verification steps, with adaptive MFA adding checks only when risk signals are detected
Single sign-on (SSO) and federation: Enabling access to multiple applications with a single set of credentials
Lifecycle management: Covering the full journey from account creation and onboarding to recovery and deactivation
Security layers: Including bot detection, risk-based checks, and session protection to guard against evolving threats
Unlike workforce authentication, which is centralized and has a relatively predictable user base, external user authentication must handle a wider range of scenarios. Consumer-focused apps, B2B platforms, partner portals, and even AI-driven agents all require different levels of flexibility, security, and user experience.
The right solution helps organizations reduce friction during sign-in, prevent fraud, stay compliant, and scale to support diverse audiences and growth goals. Let's compare some popular external user authentication solutions below.
Descope
Overview
Descope is a modern external identity and access management platform built for developers who need flexible, secure authentication without managing complex infrastructure. It is designed for both B2C and B2B SaaS applications, with built-in support for multi-tenancy, partner integrations, and even identity for AI agents and MCP ecosystems.
With native features like organization management, tenant-aware SSO, and fine-grained access controls, Descope makes it simple to scale authentication across diverse user groups and environments. It also enables secure, scoped, and consented access for AI agents and servers, helping teams prepare for emerging identity challenges.
Key capabilities
Visual workflow editor to build and modify login, signup, and MFA flows
Extensive plug & play connector ecosystem for seamless third-party integrations
Anonymous user tracking for top-of-funnel visibility
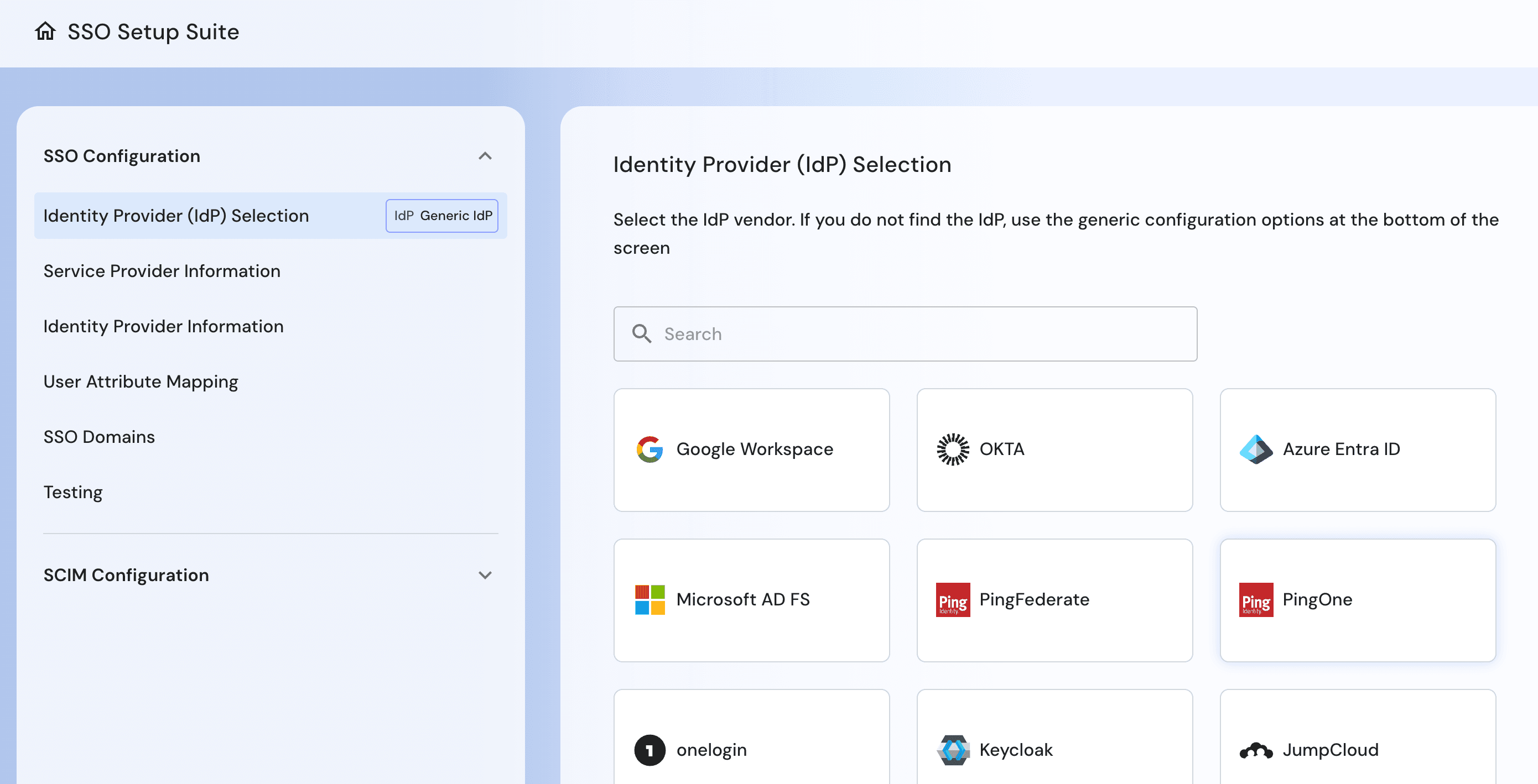
Comprehensive SSO Setup Suite, enabling self-service SSO and SCIM configuration
Embeddable UI widgets for self-service identity and administration
Wide range of authentication methods including passkeys, OTP, magic links,social login, and Google One Tap
Support for 15+ web, mobile and backend SDKs and a robust REST API
Identity orchestration to coordinate authentication, authorization, risk, and fraud tools
Agentic identity support to get agents enterprise-ready and organizations agent-ready
Strengths
Visual workflows: No-code editor simplifies auth design, reducing time to production.
Transparent pricing and support: Predictable usage-based pricing with award-winning customer support.
Streamlined SSO: Enable and manage SSO with workflows and self-service tools.
Passwordless authentication: Built-in support for passkeys, magic links, OTP, and social login.
Omnichannel authentication: Unified flows for web, mobile, and partner apps.
Adaptive MFA: Enforce MFA only when risk signals are detected, using multiple MFA options.
Enterprise agent readiness: Supports authentication for agentic AI systems with Inbound Apps, Outbound Apps, and MCP SDKs.
Developer flexibility: SDKs and APIs for modern frameworks, with options for hosted or custom UIs.
Ideal for
Descope is ideal for B2C apps and B2B SaaS apps that need multi-tenancy and tenant-aware SSO. It's also well-suited for consumer apps that seek seamless passwordless options, such as passkeys, magic links, and social logins. Developers can rely on Descope for adaptive MFA and fine-grained authorization without the overhead of traditional user authentication platforms.
Microsoft Entra External ID
Overview
Microsoft Entra External ID is a cloud-based identity solution designed to help organizations securely manage external users such as customers, partners, and suppliers. It extends the capabilities of Microsoft Entra ID to provide authentication, access management, and governance features at scale. While it is most powerful within Microsoft-centric environments, it can also be integrated with third-party applications and custom portals.
Key capabilities
Self-service registration and sign-in with social or enterprise identities
Customizable and branded user journeys for portals and external apps
Conditional access policies that evaluate context, risk, and device state
Lifecycle management with access reviews, expirations, and audit trails
Integration with Microsoft 365, Azure, and thousands of prebuilt connectors
Strengths
Enterprise alignment: Natively integrates with Microsoft infrastructure, making it a natural fit for organizations heavily reliant on Azure.
Compliance-ready: Includes governance, audit, and reporting features that meet enterprise and regulatory requirements.
Advanced security: Built-in conditional access and MFA ensure consistent protection for diverse user groups.
Ideal for
Large organizations that are already invested in Microsoft 365, Azure, or hybrid infrastructure need external identity management with strong compliance, governance, and security controls.
Okta Customer Identity Cloud (Auth0)
Overview
Okta Customer Identity Cloud, powered by the Auth0 platform, is one of the more widely recognized external identity providers. It offers hosted authentication with support for SSO, MFA, and social login, alongside enterprise features like RBAC and directory sync. While powerful, its complexity and tiered pricing can create challenges for scaling teams.
Key capabilities
Hosted login pages with branding and customization options
Support for enterprise standards including SAML, OIDC, and social identity providers
Extensibility via Actions, Hooks, and APIs for custom logic
Role-based access control and adaptive MFA
Admin dashboard for managing users, connections, and logs
Strengths
Enterprise support: Provides directory sync, federation, and SSO features suited for large organizations.
Developer ecosystem: Extensive documentation, SDKs, and a broad integration marketplace.
Proven platform: Trusted by thousands of enterprises, with strong community and partner adoption.
Ideal for
Organizations that want an enterprise-ready identity provider with broad protocol support and hosted authentication. The product is best for orgs that can manage customization complexity and higher pricing tiers in exchange for scalability and enterprise features.
OneLogin Customer Identity
Overview
OneLogin Customer Identity is an external identity solution that brings full enterprise capabilities. It provides authentication, SSO, and MFA while offering integrations with a broad set of SaaS and custom applications. After being acquired by One Identity, its struggles with uptime availability appear to have been alleviated.
Key capabilities
Centralized authentication with SSO across cloud and on-prem apps
Risk-based and adaptive MFA with multiple verification methods
Prebuilt integrations with hundreds of SaaS applications
Directory sync and user provisioning across systems
Policy-based access management for external users
Strengths
Simplified administration: Easy-to-manage console with intuitive policy setup.
Security focus: Strong MFA and risk-based authentication to reduce threats.
Integration ecosystem: A wide set of SaaS and enterprise app connectors.
Ideal for
Mid-market and enterprise organizations that want secure authentication, SSO, and MFA without the heavier customization overhead of larger CIAM platforms.
Amazon Cognito
Overview
Amazon Cognito is AWS’s native authentication and user management service, designed to secure access for web and mobile applications. It provides user sign-up, sign-in, and identity federation, with deep integration into the AWS ecosystem. While powerful for AWS-native teams, its complexity and recent pricing changes have made it challenging for some organizations to scale.
Key capabilities
User pools for managing authentication and user accounts
Identity federation with SAML, OIDC, and major social providers
AWS Lambda triggers to customize authentication flows and logic
Tight integration with AWS services such as API Gateway, AppSync, and IAM
Token-based authentication with JWT support
Strengths
Deep AWS integration: Works seamlessly with other AWS tools and services.
Flexible federation: Broad support for identity protocols beyond social login.
Custom logic: Lambda triggers allow developers to extend and tailor user journeys.
Ideal for
Organizations already building in AWS that need an authentication solution tightly integrated with the AWS ecosystem. It’s worth noting for such organizations that Descope enhances AWS-native auth with an AWS SaaS Builder Toolkit plugin that automates multi-tenant authentication, user management, and secure M2M flows.
Firebase Authentication
Overview
Firebase Authentication is Google’s lightweight identity solution built into the Firebase platform. It offers quick setup for common authentication methods and integrates tightly with Firebase services like Firestore, Cloud Functions, and Firebase Hosting. It is especially popular with mobile-first developers and startups who want to launch quickly without managing infrastructure.
Key capabilities
Support for email/password, phone authentication, and social logins
Anonymous sign-in for guest user sessions
Prebuilt UI libraries for web, iOS, and Android apps
SDK integration across major platforms, including Flutter
Native connections with other Firebase services for a unified developer experience
Strengths
Fast setup: Developers can enable and configure authentication in minutes.
Mobile-first focus: Strong support for Android, iOS, and cross-platform frameworks.
Tight ecosystem integration: Works seamlessly with Firebase tools like Firestore and Cloud Functions.
Ideal for
Startups and small teams that need a plug-and-play authentication solution to get to market quickly. It is best suited for mobile-first applications that rely heavily on Firebase or Google Cloud services. Still, teams should be cautious of vendor lock-in, as migrating away from Firebase often requires significant architectural changes.
Keycloak
Overview
Keycloak is an open-source identity and access management solution originally developed by Red Hat. Keycloak is fully self-hosted, giving organizations maximum control over their authentication stack. It supports modern protocols like OIDC and SAML, as well as integration with LDAP directories, making it well-suited for enterprises with hybrid or legacy systems.
Key capabilities
Self-hosted deployments with clustering and high availability
Built-in admin console for managing users, roles, and authentication realms
Customizable login pages and authentication flows
Native support for OIDC, SAML, and LDAP
Fine-grained role-based and attribute-based access control
Strengths
Full control: Complete customization of authentication, authorization, and user management.
Protocol flexibility: Strong support for enterprise standards like SAML and LDAP.
Vendor-neutral: Open-source with no licensing costs, deployable on any infrastructure.
Ideal for
Organizations with DevOps resources that want to self-host and customize their authentication system. Keycloak is best for enterprises needing maximum flexibility and protocol coverage, but it comes with the tradeoff of higher operational overhead.
Supabase Auth
Overview
Supabase Auth is the authentication service within the open-source Supabase platform, built as a developer-friendly authentication option. It provides out-of-the-box support for email, passwordless, and third-party logins, all backed by a Postgres database for strong access control.
Key capabilities
Email/password, magic link, and third-party OAuth provider support
Postgres-based authentication with row-level security
Serverless edge functions for custom backend logic
SDKs for JavaScript, Flutter, and other frameworks
Option to deploy fully managed or self-hosted environments
Strengths
Open-source and transparent: No lock-in, with the option to self-host.
Postgres integration: Leverages native Postgres features for fine-grained access control.
Flexible deployment: Teams can choose a hosted service for speed or self-host for control.
Ideal for
Developers and startups who want Firebase-style simplicity with more backend control and the option to self-host. Supabase is a natural fit for MVPs, and many teams use it as their database from day one. With Descope, they can keep Supabase as their data layer while upgrading to advanced authentication and authorization, avoiding vendor lock-in and eliminating the need to re-platform as they scale.
Also read: Supabase + Descope sample app
Also read: Next.js integration guide
Conclusion
External user authentication is foundational to every digital product, but the right solution depends on your stack, audience, and growth goals. Some solutions are excellent for getting started quickly, yet, as teams grow, more flexibility, scalability, or governance features become a higher priority than those solutions can provide. From the self-hosting power of Keycloak to the enterprise governance of Microsoft Entra External ID, each provider brings their own strengths to the table.
Descope stands out for developers who want customizable, no-code authentication flows, built-in multi-tenant support, and the ability to extend authentication to partners, MCP servers, and even AI agents. It combines developer-friendly design with enterprise-grade security and transparent pricing, making it a strong fit for both startups and scaling organizations.
For more detailed information on Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account and start dragging & dropping your auth today!