Table of Contents
What is Dynamic Client Registration (DCR)?
One of the most pressing issues in contemporary computing is whether and how agentic models can speak to one another. The biggest breakthrough in recent years was the emergence of the Model Context Protocol (MCP), which standardizes communication and connections among large language models (LLMs) such as ChatGPT, Gemini, and other artificial intelligence (AI) tools.
Two of the most critical protocols for agentic identification are Dynamic Client Registration (DCR) and Client ID Metadata Documents (CIMD). DCR has been around longer, but CIMD is making waves in developer circles. It’s imperative to understand both to make informed decisions about how AI agents and other programs are authenticated in any project.
To that effect, this guide will cover:
What DCR is and how it works
What CIMDs are and how they work
The differences between DCR and CIMD
When to choose either DCR or CIMD
Security considerations for DCR and CIMD
What is Dynamic Client Registration (DCR)?
Dynamic Client Registration (DCR) is a protocol defined by the Internet Engineering Task Force (IETF) in RFC 7591. It’s used by Open Authorization (OAuth) and Open ID Connect (OIDC) systems to facilitate client applications registering on authorization servers. Specifically, it allows automatic, programmatic registration (without manual pre-registration) for a faster workflow.
DCR plays an important role in client onboarding and OAuth/OIDC workflows. It allows clients to discover auth servers and registration endpoints, which in turn allows for automated metadata submission. It receives client credentials and enables their immediate use in OAuth/OIDC flows.
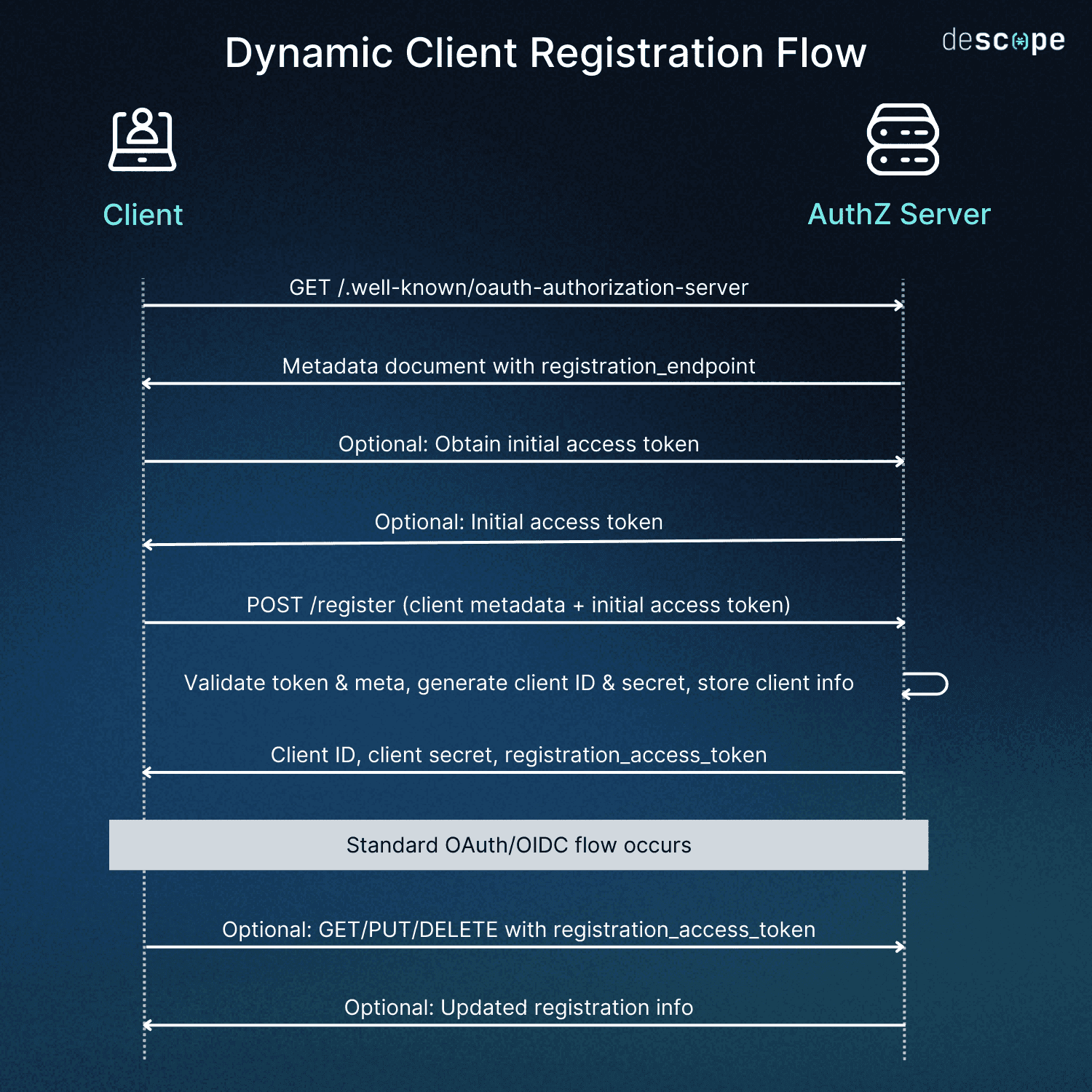
This is what enables DCR to programmatically register clients with an authorization server.
DCR emerged to solve bottlenecks in specific tech environments. For instance, open ecosystems that add applications are often slowed by manual registrations. As such, DCR has proven useful in distributed systems, mobile app development, and systems with dynamic trust relationships.
However, as MCP environments grow to include short-lived or automatically generated clients—such as CI/CD runners, IDE extensions, and agentic submodules—DCR can become increasingly difficult to maintain. Each temporary client registration adds to server storage and management overhead, often leading to unnecessary churn and slower performance at scale.
These challenges have prompted many teams to explore more flexible alternatives like CIMD, which eliminate the need for persistent registry maintenance.
What is a Client ID Metadata Document (CIMD)?
Client ID Metadata Documents (CIMD) emerged in late 2025 as an alternative to DCR client ID on open, federated networks. While the underlying technology had already been in use by some innovative developers for quite some time, it gained popularity as many MCP stakeholders faced frustrations with DCR’s operational efficiency.
CIMD uses URL-hosted metadata as an identifying factor for agents. This allows clients to identify themselves swiftly without needing to register with every new server individually.
In CIMD, the client’s JavaScript Object Notation (JSON) metadata is fetched through a stable Hypertext Transfer Protocol Secure (HTTPS) URL. Replacing server-side registration allows for the same or better security assurances with greater capacity for efficiency at scale.
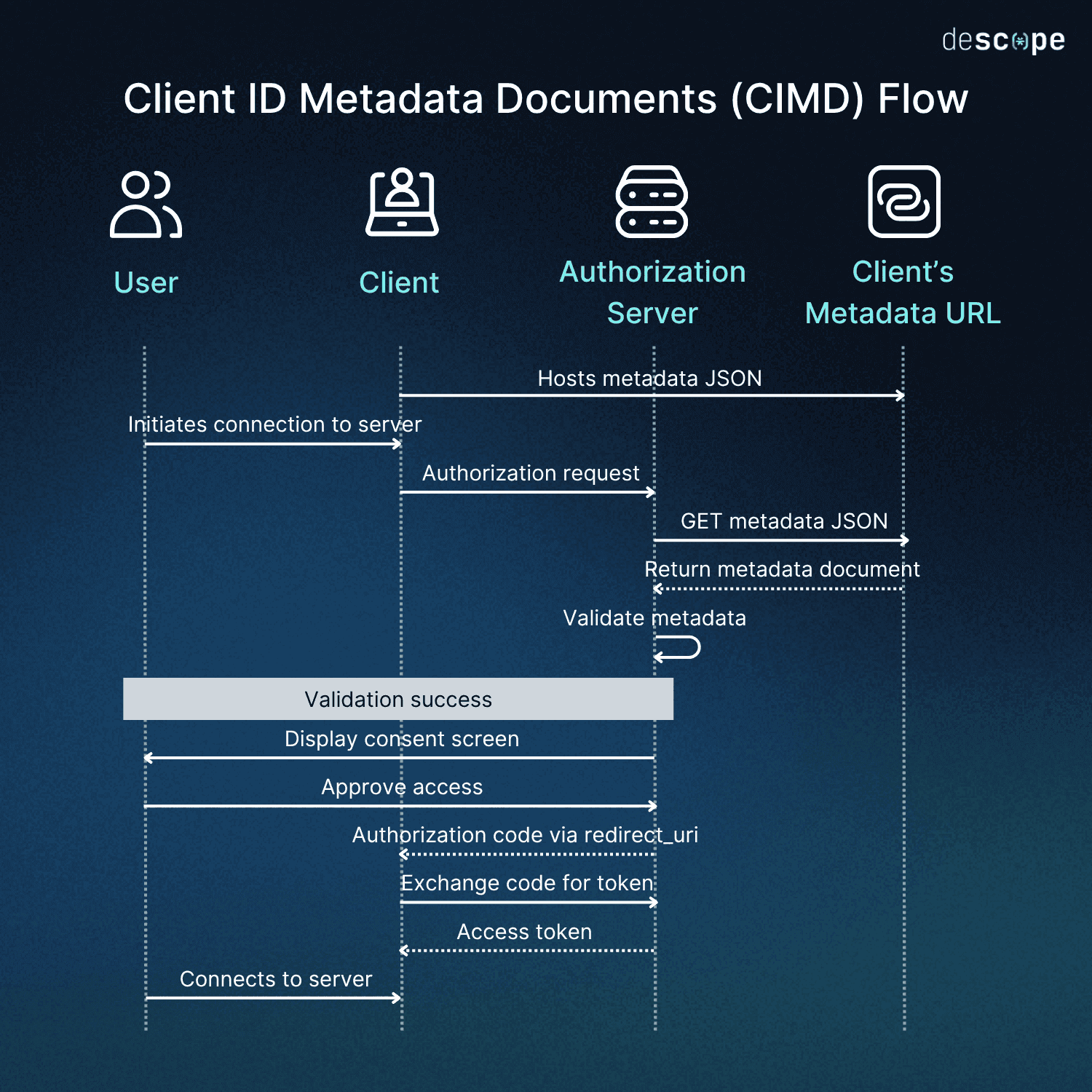
Recent specification changes across the MCP exacerbated underlying MCP client registration and management challenges. DCR, while widely used, is prone to operational issues for both auth servers and clients due to unbound database growth and the associated overhead. It’s also susceptible to client identity impersonation schemes, the risk of which grows with scale.
For these reasons, CIMD is especially relevant in MCP contexts where:
There is rapid, sustained growth in complexity
Servers and clients regularly need to dynamically discover one another
Core differences between DCR and CIMD
Both DCR and CIMD exist to serve the same basic function: facilitating agent identification across the MCP. The ways they approach the problem differ, as do their use cases, but they’re ultimately two sides of the same coin. CIMD emerged to solve the same problems DCR did.
Here’s how the two protocols stack up, at-a-glance, across the most important factors:
| DCR | CIMD |
|---|---|---|
Registration model | Server-centered | Client-hosted |
State management | Persistent registry | On-demand fetching |
Protocol scalability | Difficult to maintain at scale | Inherent stateless scalability |
Security considerations | Open registration endpoints | URL-based ID verification |
Operational complexity | Server storage challenges | Large-scale metadata hosting |
Deciding which protocol to use depends on the level of complexity and the need for efficiency in a given MCP environment. Those with greater needs will likely lean toward CIMD, while dev teams already using DCR effectively may not need to switch—at least not yet.
When to choose DCR
DCR was formerly the default method for MCP client registration, but it’s no longer the default or the consensus best option. However, there are scenarios where DCR is still worth using.
For example, projects or environments with highly curated client lists or long-lived clients may opt to keep using what has worked historically for as long as possible. This is also true for large enterprise systems with many legacy programs or tight governance that makes change difficult.
However, even in these situations, the limitations and risks of DCR mentioned above need to be taken into consideration. Implementing DCR best practices to harden client registration will help insulate your system. Consider building a layered verification process, limiting registrations based on their source, implementing risk-based controls, and using short-lived sessions.
For most developers, CIMD is a better option than DCR. DCR client ID is best suited to niche situations where the costs of switching to or implementing CIMD outweigh its benefits.
When to choose CIMD
CIMD has overtaken DCR as a preferred default method for client registration in MCP, and it’s better for most use cases. It does everything DCR does while addressing several of its weaknesses.
There are some situations in which CIMD is especially beneficial and should almost certainly be used, even if switching from DCR or another protocol might be challenging. Open ecosystems and environments with highly dynamic agent fleets will see the most benefit from using CIMD.
However, CIMD can be somewhat complex to implement. Hosting metadata, caching, and domain verification operations all need to be accounted for. Dev teams without sufficient resources in place might need to delay what’s likely an inevitable switch.
As noted above, CIMD is the optimal choice in most situations. It’s not strictly binary; developers can make room for both CIMD and DCR flows. But CIMD is usually better.
In practice, many teams adopt a hybrid approach. For instance, DCR can remain in place for long-lived or enterprise-managed clients that require structured oversight, while CIMD can handle dynamic or frequently instantiated agents that need faster, on-demand discovery. This allows developers to retain control where necessary while still benefiting from CIMD’s scalability.
Security considerations for DCR and CIMD
Both DCR and CIMD offer better security than any system that relies more heavily on manual client registration. By removing or at least minimizing the human element, both protocols reduce the attack surface across client ID and the MCP more broadly. But neither tool is without risks.
On the DCR side, there are well-known registration endpoint abuse vulnerabilities that need to be accounted for. In the simplest terms, DCR systems can be overwhelmed with junk requests that exacerbate underlying operational issues and expose flaws that attackers can exploit. This can lead to client impersonation, as mentioned above, along with redirect and other attacks.
On the CIMD side, dev teams need to contend with concerns around metadata authenticity, complex validation needs, and related risks. CIMD is still new, and risks are still emerging. One significant threat vector to watch out for is the potential for Server Side Request Forgery (SSRF) attacks, where attackers can modify URLs to compromise the otherwise seamless fetching workflow.
The hardening methods alluded to above have worked well in mitigating DCR vulnerabilities and can be adapted to CIMD systems. Using a robust auth platform to streamline all elements of Identity and access management (IAM) for agentic and other clients can further strengthen your defenses.
Implement DCR and/or CIMD with Descope Agentic Identity Hub
Dynamic Client Registration and Client ID Metadata Documentation represent two distinct paths to automating client onboarding and identity in modern MCP ecosystems. CIMD recently overtook DCR as the preferred default in these systems, but both protocols offer value in different use cases. Dev teams should prioritize auth solutions that accommodate DCR, CIMD, and other emerging client ID solutions.
The Descope Agentic Identity Hub is a dedicated identity provider for AI agents and MCP servers that helps MCP developers support both DCR and CIMD as client registration methods with the switch of a toggle.
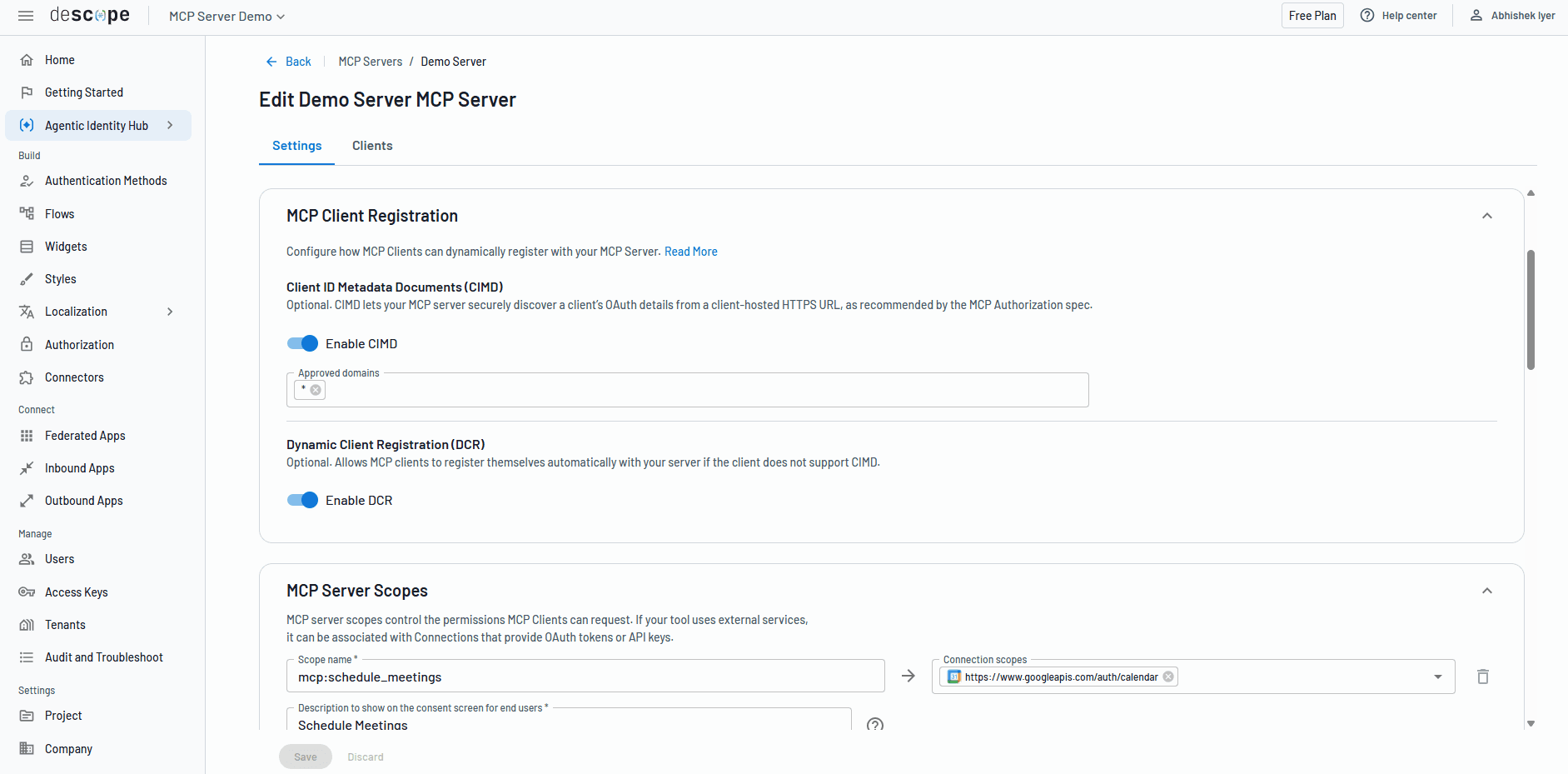
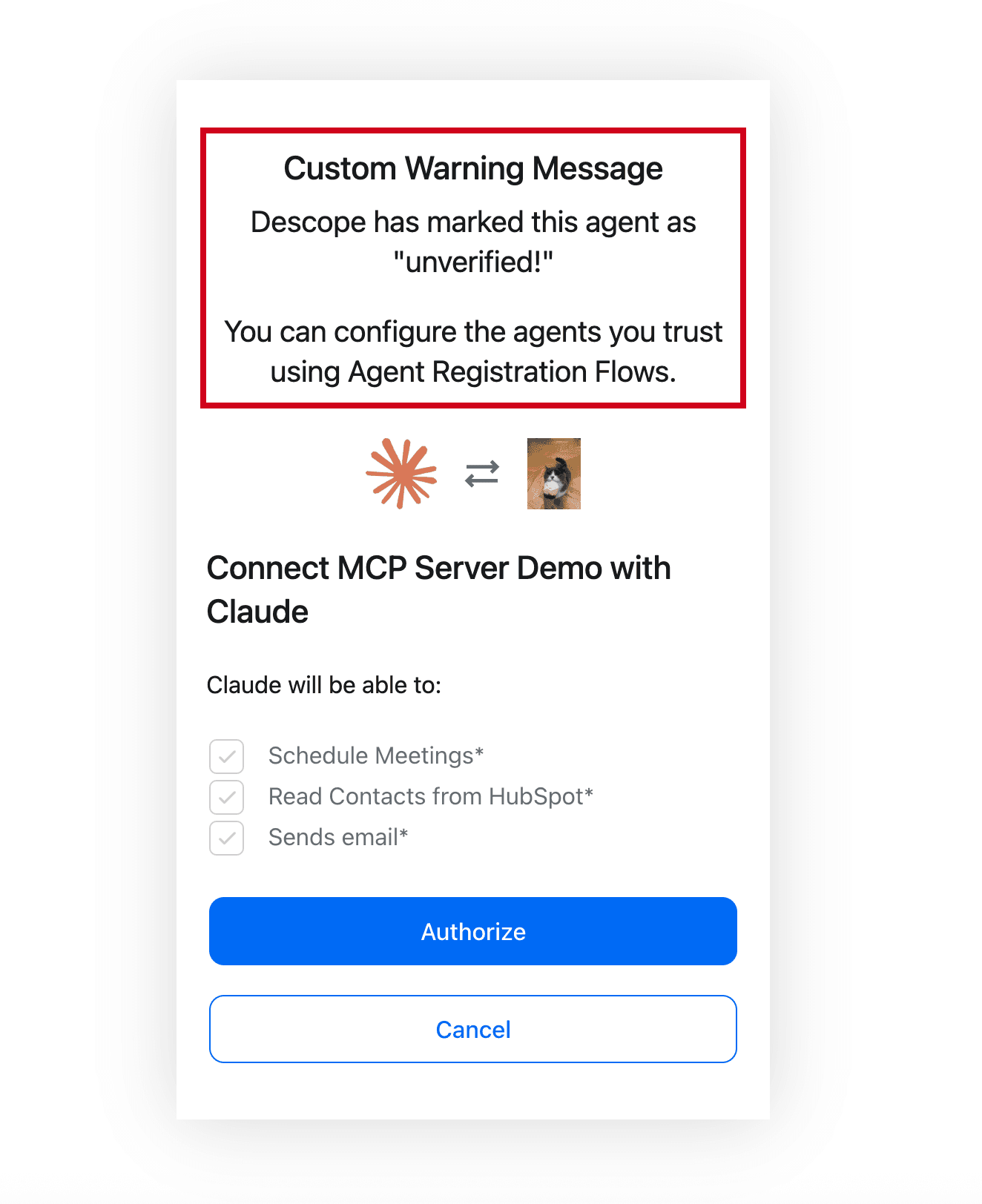
Descope also mitigates some of the security risks inherent to DCR by providing agent risk assessment flows–agents go through a customizable risk assessment check during time of registration (e.g. IP address checks, geo checks, third-party risk scores). Based on the agent’s risk level, organizations can mark it as “unverified”, show warning signs to end users during consent flows, assign the agent read-only scopes, or block the agent’s access altogether.
Sign up for a Free Forever account with Descope and start building secure, scalable auth flows today. Have questions about DCR and CIMD workflows in MCP servers? Book time with our experts.