Table of Contents
What is SCIM?
System for Cross-domain Identity Management (SCIM) is the foundation of automated, secure user lifecycle management in B2B SaaS applications. It defines how users are provisioned, updated, and deprovisioned, ensuring access stays accurate as organizations, teams, and employees change. By syncing identities directly from enterprise directories, SCIM eliminates manual user management and keeps tenant environments clean and consistent.
From early-stage B2B products to enterprise SaaS platforms, SCIM has become a core requirement for modern onboarding architecture. The right SCIM implementation makes it easier to support delegated administration, directory-driven access control, and audit-ready user management without introducing brittle scripts or manual workflows. For developers, SCIM is no longer just an IT checkbox, but a product capability that directly impacts enterprise adoption, security posture, and operational scalability.
In this guide, we explore the top SCIM providers for B2B SaaS applications. We break down how each solution approaches provisioning and deprovisioning, highlight key strengths and tradeoffs, and explain which types of teams and products are best suited for each platform.
What is SCIM?
SCIM is a standardized protocol that automates user provisioning, updates, and deprovisioning between identity providers and SaaS applications. Instead of manually creating and managing users inside each application, SCIM allows organizations to control the entire user lifecycle directly from their identity system, such as Okta or Microsoft Entra ID. This approach reduces operational overhead and ensures access stays accurate and up to date.
Modern SCIM extends beyond simple user creation. In B2B SaaS applications, SCIM must operate in multi-tenant environments where each customer organization manages its own users, groups, and lifecycle policies independently. Effective SCIM implementations support tenant-scoped provisioning, group-based access control, and real-time deprovisioning, ensuring user state remains consistent as employees join, move between teams, or leave an organization.
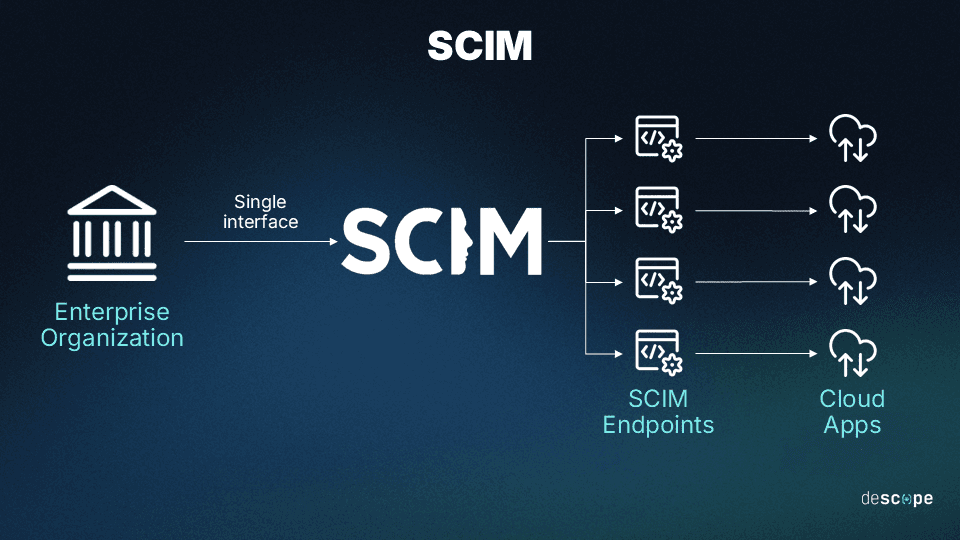
Core components of SCIM typically include:
Users: Standardized user objects that represent individuals and their attributes, such as email, name, and status.
Groups: Collections of users managed in the directory and synchronized to the application to drive access and role assignments.
Provisioning: Automated creation and updating of users in the application when changes occur in the identity provider.
Deprovisioning: Immediate suspension or removal of users when access is revoked in the directory.
Schemas and mappings: Standard attribute definitions and transformations that align directory data with application-specific user models.
Administration tools: APIs and configuration interfaces that allow tenant admins to connect their directory, manage mappings, and monitor provisioning activity.
Unlike user management for internal IT systems, SCIM for B2B SaaS must scale across many external customer organizations. Each tenant requires isolated provisioning, independent administrators, and strict separation of user data, all while maintaining a consistent and reliable product experience.
The right SCIM solution helps developers deliver automated, secure user lifecycle management that scales with their application. Below, we compare seven leading SCIM providers designed to support multi-tenant B2B SaaS platforms and enterprise-ready onboarding workflows.
What to consider when choosing a SCIM provider for B2B SaaS
Choosing the right SCIM provider depends on your application’s architecture, customer onboarding model, and long-term enterprise strategy. While many platforms offer basic user synchronization, B2B SaaS environments require stronger tenant isolation, reliable deprovisioning, and tight alignment with enterprise identity workflows.
Key factors to evaluate include:
Multi-tenant provisioning architecture - Support for tenant-scoped SCIM configurations so each customer organization can independently provision and manage users without impacting other tenants.
SCIM 2.0 standards compliance - Full support for standardized SCIM endpoints, schemas, filtering, pagination, and patch operations to ensure compatibility with enterprise identity providers.
Group and role mapping - The ability to map directory groups to application roles or permissions, enabling directory-driven access control without manual user management.
Deprovisioning reliability - Immediate and deterministic user deactivation when access is removed in the identity provider, reducing security risk and orphaned accounts.
SSO alignment - Native integration with SAML or OIDC SSO so provisioning and authentication remain consistent throughout the user lifecycle.
Administration experience - Self-service configuration and visibility for tenant admins, including attribute mappings, group assignments, and provisioning status, without vendor support tickets.
Operational visibility and auditing - Logs, error reporting, and audit trails that help teams monitor provisioning activity and troubleshoot failures at scale.
Developer experience - Clear APIs, SDKs, and documentation that make it easy to implement SCIM correctly without building custom lifecycle logic or maintaining brittle integrations.
Scalability and enterprise readiness - A proven ability to handle large directories, frequent updates, and compliance requirements across many customer organizations.
A strong SCIM solution balances automation, reliability, and usability, enabling teams to deliver frictionless enterprise onboarding while maintaining secure and predictable user lifecycle management.
With these considerations in mind, let’s explore the top SCIM providers for B2B SaaS applications.
Descope
Overview
Descope is a modern customer identity platform designed to simplify SCIM-based user provisioning, enterprise SSO, and access lifecycle management for B2B SaaS applications. It enables teams to automate user creation, updates, and deprovisioning directly from customer identity providers, keeping tenant environments accurate and secure without manual user management or brittle integrations.
Descope’s native SCIM implementation is built for multi-tenant SaaS, allowing each customer organization to independently provision and manage users while maintaining strict tenant isolation. The same user can exist across multiple organizations with separate identities, roles, and lifecycle policies, ensuring user state stays consistent as teams, departments, and employment status change.
Beyond provisioning, Descope tightly integrates SCIM with enterprise-ready authentication and access workflows, including SAML and OIDC SSO, role-based access control, and delegated administration. Tenant admins can configure SCIM, map directory groups to application roles, and manage user lifecycle events through self-service setup flows, reducing onboarding friction and operational overhead.
With visual workflows and SDKs for modern frameworks, Descope unifies SCIM provisioning, SSO, authentication, and authorization into a single, developer-friendly platform, enabling teams to deliver reliable enterprise onboarding and scalable identity management from day one.
Key capabilities
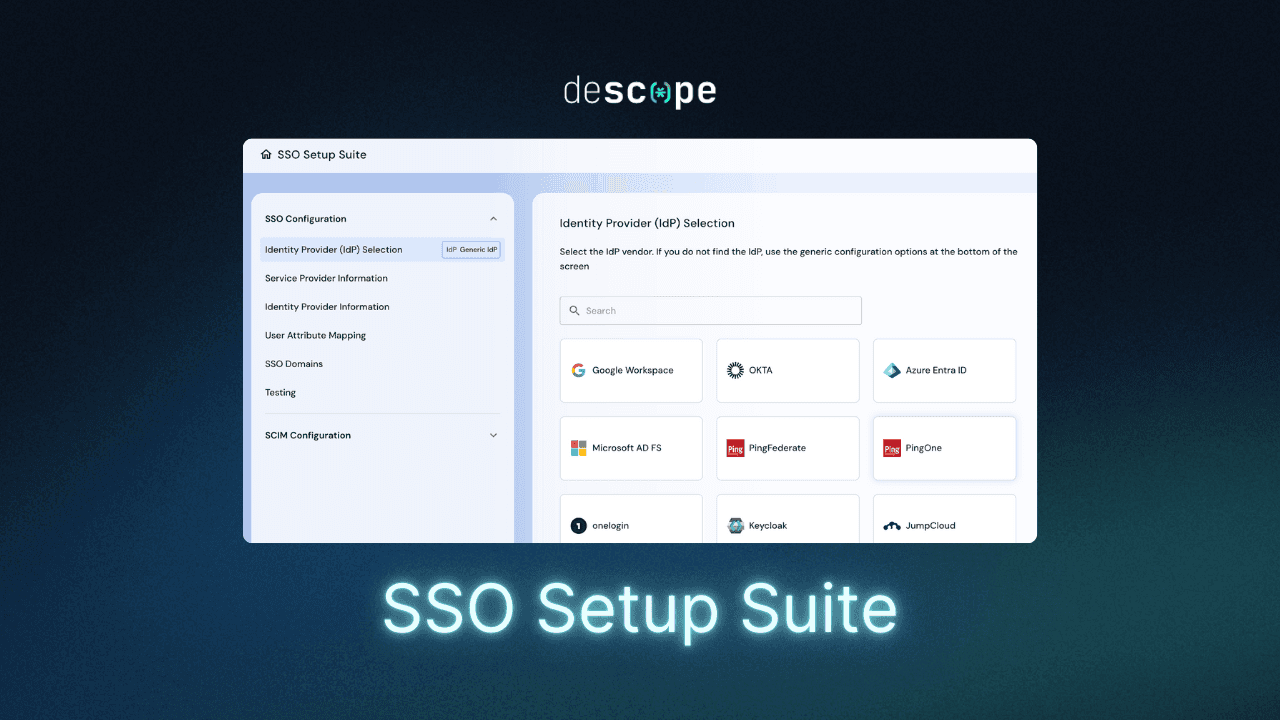
Guided SCIM configuration for tenant admins: Descope’s SSO Setup Suite provides a guided, self-service experience that helps customer admins configure SCIM provisioning quickly and correctly.
Tenant-aware SCIM provisioning: Automate user creation, updates, and deprovisioning per organization, ensuring accurate user lifecycle management and strict tenant isolation across B2B SaaS environments.
Group and attribute mapping: Map directory users and groups to application roles and permissions, enabling directory-driven access control without manual user management.
Enterprise SSO support: Enable SAML and OIDC-based SSO for customer tenants, tightly aligned with SCIM provisioning and access policies.
Comprehensive passwordless authentication: Support for passkeys, OTP, magic links,social login, and Google One Tap, giving users multiple secure, frictionless ways to sign in without passwords.
Visual workflow editor: Drag and drop passwordless and MFA flows to design custom login experiences without writing backend code.
Adaptive MFA and security controls: Protect accounts with context-aware MFA, session management, and bot detection that respond dynamically to risk.
Prebuilt UI widgets: Quickly embed self-service passwordless auth (e.g. adding passkeys and authenticator apps) and account recovery components (e.g. resetting passwords) into any web or mobile app.
SDKs and APIs for modern frameworks: Broad developer coverage across 15+ SDKs, including Next.js, Flutter, React Native, and more.
Connector ecosystem: Integrate seamlessly with third-party tools for risk, fraud, analytics, and directory sync.
Integration-ready orchestration: Enrich user journeys with data and actions from third-party fraud, go-to-market, and compliance tools.
Agentic identity support: Secure and manage consented access for AI agents and MCP ecosystems alongside human users.
Strengths
B2B-first SCIM architecture: Native support for tenant-aware provisioning enables automated user lifecycle management across multi-tenant SaaS environments without cross-tenant risk.
Reliable deprovisioning by default: Immediate user suspension or removal when access is revoked in the directory helps eliminate orphaned accounts and reduces security exposure.
Enterprise-aligned identity workflows: Tight integration between SCIM, SSO, and access controls ensures user state stays consistent across authentication, authorization, and onboarding workflows.
Fast enterprise onboarding: Self-service SCIM setup and directory mapping reduce implementation time and minimize support involvement during customer rollout.
Directory-driven access control: Group and attribute mapping allow enterprises to manage user access centrally without manual invites or in-app user administration.
Consistent lifecycle enforcement: Centralized provisioning logic ensures predictable user creation, updates, and removals across services and environments.
Developer-first platform: Clear APIs, SDKs, and documentation simplify implementing SCIM correctly without maintaining custom provisioning logic.
Scales with customer growth: Designed to support everything from early-stage B2B products to large, multi-tenant SaaS ecosystems with high user churn.
Transparent pricing and reliable support: Usage-based pricing and responsive developer support help teams adopt SCIM confidently as enterprise demand grows.
Ideal for
Descope is ideal for developers and product teams building B2B SaaS applications that require tenant-aware SCIM provisioning, enterprise SSO, and automated user lifecycle management without managing complex identity infrastructure. It works well for startups establishing enterprise-ready onboarding early and for mature SaaS platforms modernizing provisioning across multi-tenant environments. With Descope, teams can deliver reliable, directory-driven user management that scales seamlessly as customers, organizations, and user counts grow.
Also read: How You.com Reduced SSO / SCIM Onboarding Times to 15 Minutes With Descope
Auth0
Overview
Auth0, part of Okta, is a widely used identity platform that supports SCIM provisioning as part of its broader enterprise authentication and customer identity capabilities. Auth0 enables B2B SaaS teams to automate user creation, updates, and deprovisioning from enterprise identity providers, aligning user lifecycle management with SSO and federation workflows. Auth0’s SCIM implementation is typically used to sync users and groups from customer directories into Auth0-backed applications.
While effective for standard provisioning scenarios, SCIM in Auth0 often requires additional configuration to align directory groups with application-specific roles, especially in multi-tenant SaaS environments. As deployments scale, teams may rely on custom Actions, rules, or downstream logic to manage tenant context, delegated administration, and role mapping.
Key capabilities
SCIM 2.0 provisioning for automated user lifecycle management
User and group synchronization from enterprise identity providers
Integration with SAML and OIDC-based SSO
Attribute mapping and user profile updates via directory sync
Strengths
Enterprise-ready provisioning: Proven SCIM support used by many large organizations for directory-driven onboarding.
Broad IdP compatibility: Works with major enterprise identity providers and federation setups.
Mature ecosystem: Extensive documentation, SDKs, and a large partner and developer community.
Ideal for
Organizations that want a well-established identity platform with SCIM provisioning tightly coupled to authentication and SSO. Auth0 is best suited for teams that are comfortable managing additional configuration and tenant-specific logic to support SCIM in multi-tenant B2B SaaS environments, in exchange for enterprise adoption and ecosystem maturity.
Microsoft Entra External ID
Overview
Microsoft Entra External ID provides identity and access management for external users, including customers and partners, within the Microsoft ecosystem. It supports SCIM provisioning to automate user creation, updates, and deprovisioning from enterprise directories, aligning user lifecycle management with Microsoft-based identity workflows.
SCIM integrates closely with Entra ID and Azure services, making it a strong fit for Microsoft-first enterprises, though multi-tenant SaaS implementations often require additional configuration to manage tenant context and group mapping.
Key capabilities
SCIM provisioning for automated user lifecycle management
User and group synchronization from Microsoft Entra ID tenants
Integration with SAML and OIDC-based enterprise SSO
Role and group assignments delivered via token claims
Strengths
Microsoft-aligned provisioning: Native fit for organizations standardized on Microsoft Entra.
Enterprise-grade reliability: Backed by Microsoft’s global identity, security, and compliance infrastructure.
Standards-based integration: Uses widely adopted protocols for provisioning and authentication.
Ideal for
B2B SaaS applications targeting Microsoft-centric enterprises that want SCIM provisioning aligned with Entra identity models.
OneLogin
Overview
OneLogin is an established identity and access management platform that supports SCIM provisioning as part of its enterprise IAM offering. It enables automated user creation, updates, and deprovisioning from customer directories into SaaS applications, helping reduce manual onboarding and offboarding work.
OneLogin’s SCIM capabilities follow standard patterns and integrate closely with its SSO workflows, though tenant-aware provisioning and role mapping for multi-tenant B2B SaaS often require additional application-side logic.
Key capabilities
SCIM provisioning for automated user lifecycle management
User and group synchronization from enterprise directories
Integration with SAML and OIDC-based SSO
Attribute mapping and directory-driven user updates
Strengths
Mature IAM platform: Longstanding presence in enterprise identity and provisioning.
Standards-based SCIM support: Compatible with common enterprise directory setups.
SSO and provisioning alignment: SCIM works alongside OneLogin’s authentication workflows.
Ideal for
B2B SaaS applications serving traditional enterprise customers that already use OneLogin. It is best suited for teams that need standard SCIM provisioning and are prepared to handle tenant isolation and role mapping logic within their application.
Keycloak
Overview
Keycloak is an open-source identity and access management platform that supports SCIM-style user provisioning through extensions and custom integrations. While SCIM is not a first-class feature out of the box, Keycloak can be configured to synchronize users and groups from external directories into applications.
For B2B SaaS teams, implementing SCIM with Keycloak typically requires additional setup, custom development, and ongoing operational management to support multi-tenant provisioning reliably.
Key capabilities
User and group management with extensible provisioning workflows
Support for SCIM-like provisioning via plugins or custom integrations
Integration with SAML, OIDC, and OAuth 2.0
Flexible role and group modeling through realms and clients
Strengths
Open-source control: Full ownership and customization of identity infrastructure.
Flexible architecture: Can be adapted to support custom provisioning requirements.
Standards-compliant: Broad protocol support for enterprise authentication and federation.
Ideal for
B2B SaaS teams that prefer an open-source identity solution and have the engineering and operational capacity to build, host, and maintain SCIM provisioning themselves.
Authentik
Overview
Authentik is an open-source identity provider that supports SCIM provisioning for synchronizing users and groups from enterprise directories into applications. It enables automated user lifecycle management and integrates SCIM with its SSO and authentication workflows.
While flexible, Authentik’s SCIM implementation is infrastructure-centric, and supporting tenant-aware provisioning for multi-tenant B2B SaaS often requires additional configuration and operational ownership.
Key capabilities
SCIM provisioning for automated user creation and deprovisioning
User and group synchronization from external identity providers
Integration with SAML and OIDC-based SSO
Extensible configuration through policies and flows
Strengths
Open-source and flexible: Full control over identity and provisioning behavior.
Modern architecture: Actively developed with a growing community.
SSO and SCIM alignment: Provisioning works alongside authentication flows.
Ideal for
B2B SaaS teams that prefer an open-source identity platform and are comfortable managing infrastructure and configuration themselves.
Ory Polis
Overview
Ory Polis is Ory’s policy and authorization service, designed to externalize access control and identity-related decisions from application code. While Polis itself is not a dedicated SCIM provider, it is often used alongside Ory’s broader identity stack to support user and access lifecycle workflows in distributed systems.
In B2B SaaS environments, SCIM-style provisioning typically requires pairing Polis with additional Ory components or custom services to handle directory-driven user creation, updates, and deprovisioning.

Key capabilities
Policy-based access control integrated with Ory’s identity stack
API-driven management of users, relationships, and access decisions
Designed to work with external identity sources and custom provisioning flows
Scalable, cloud-native architecture for distributed systems
Strengths
Authorization-first design: Built to externalize and centralize access logic across services.
Flexible architecture: Can be composed with custom SCIM or provisioning services.
Cloud-native scalability: Designed for high-throughput, distributed environments.
Ideal for
B2B SaaS teams that want a developer-first identity platform with basic SCIM provisioning and are able to handle tenant isolation, role mapping, and authorization logic within their own application.
Conclusion
Modern SCIM is no longer just a backend integration for IT teams. It has become a core part of how B2B SaaS products onboard enterprise customers, manage access securely, and scale user lifecycle operations with confidence. The right SCIM solution automates provisioning and deprovisioning, simplifies tenant administration, and ensures user access stays accurate as organizations, teams, and employees change. Whether your goal is to accelerate enterprise onboarding, reduce security risk, or eliminate manual user management, adopting a reliable and tenant-aware SCIM platform is essential.
Among today’s options, Descope stands out for its native support for tenant-aware SCIM provisioning, enterprise SSO, and directory-driven access control, all delivered through a unified, developer-friendly platform. By tightly integrating SCIM with authentication and authorization, Descope enables teams to deliver consistent, automated user lifecycle management without stitching together multiple tools or maintaining brittle integrations.
To learn more about implementing SCIM with Descope, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account and start building enterprise-ready onboarding and provisioning today!