Table of Contents
What is policy-based access control?
Modern organizations can’t afford to treat access control as a static checklist item. Between hybrid workforces, multi-cloud environments, and ever-changing compliance demands, businesses need an authorization model that’s as dynamic as their operations. Policy-based access control (PBAC) offers that flexibility, using centrally governed policies to deliver secure, seamless, and scalable authorization.
In this guide, we’ll break down what PBAC is, how it compares to other access models, its benefits and challenges, and best practices for implementation—so you can decide if PBAC is the right next step for your organization.
Main points
Dynamic security for dynamic environments – PBAC adapts to hybrid workforces, multi-cloud systems, and evolving compliance needs without adding friction for users.
Centralized policies, consistent control – A single source of truth for access decisions simplifies management, strengthens security, and streamlines audits.
Fine-grained, context-aware authorization – Decisions consider user identity, device, location, and risk signals to grant the right level of access at the right time.
Scalability with strategy – With proper governance and testing, PBAC can scale smoothly, supporting growth while reducing operational overhead.
What is policy-based access control?
Policy-based access control (PBAC) is an approach to identity and access management (IAM) that determines authorization based on organizational or regulatory policies. Rather than granting access to data automatically or restricting access based on static characteristics, a PBAC system grants or denies access (and other) requests by referencing centrally managed policy mandates.
Rules written in human-readable and/or machine-readable formats tell automated PBAC systems how to operate. When users make requests, platforms determine whether to allow a certain behavior or not—and why—because the specific reasons for doing so have been pre-programmed.
PBAC vs. RBAC vs. ReBAC vs. ABAC
One of the best ways to appreciate PBAC’s functionality is to compare it to similar approaches to access control. While PBAC is often used interchangeably with these approaches, it differs in terms of authorization rules.
These approaches include, but are not limited to:
Role-based access control (RBAC) – Determines whether a user can access a data environment based on their role as defined by the system (i.e., job title or description). It’s easier to set up in static environments but less adaptable at scale.
Relationship-based access control (ReBAC) – Adds a wrinkle to RBAC by determining authorization based on relationships between the user and the environment in question. It offers better granularity but is more complex and harder to maintain.
Attribute-based access control (ABAC) – Authorizes access based on one or more characteristics (attributes) present in the context of the request. It maximizes flexibility and control but can be difficult to manage and lacks centralized policy governance.
PBAC builds on concepts found in ABAC but with centralized governance and versioned policies for greater consistency and control across systems.
Key components of PBAC
Policies are the beating heart of PBAC. They establish conditions and actions, determining who gets to access what and under what circumstances. To function effectively, policies should be clearly defined, versioned, and updated regularly to ensure that compliance and security needs are met.
Other critical components include:
Policy Decision Point (PDP) – Evaluates whether and how the rules apply to a given situation.
Policy Enforcement Point (PEP) – Enacts those decisions in real time, granting, revoking, or limiting access based on the defined policies.
Contextual Inputs – Signals like user identity, device, geographical location, IP address, time of request, and environmental risk indicators, which inform the decision-making process.
How PBAC works
While the technical components under the hood might seem complicated, the process that powers PBAC is straightforward when policies are properly structured and tested.
Here’s how an access request under PBAC works in practice:
A user requests access to a protected resource.
The request is sent to the PEP.
The PEP checks with the PDP.
Applicable policies are evaluated against context and attributes.
The PDP returns a decision (e.g., grant, deny, step up authentication, limit access).
From the user’s perspective, this process is seamless. Behind the scenes, PBAC ensures sensitive data is only accessible to the right users, under the right conditions.
Benefits of PBAC
PBAC offers a range of advantages to IT, security, and compliance teams:
Fine-grained control – Granular, context-aware authorization helps reduce privilege creep and insider threat risk by ensuring users only have access to the data, systems, or environments they need—and only when they need them. This dynamic flexibility is especially valuable in organizations with hybrid workforces or BYOD environments.
Centralized consistency – Unified, centrally managed policies eliminate conflicting permissions across applications and platforms. This not only strengthens security but also simplifies administration in complex hybrid or multi-cloud environments.
Auditability and compliance – Versioned, traceable policies make it easier to demonstrate compliance with frameworks like HIPAA, SOX, GDPR, PCI DSS, and ISO 27001. What used to take days of manual audit preparation can often be handled in hours, reducing operational stress and regulatory risk.
Operational efficiency – By automating policy enforcement, PBAC reduces the time IT and security teams spend manually managing roles and permissions. That bandwidth can instead be dedicated to higher-impact projects, like improving security posture or optimizing user experience.
Business agility – Dynamic policies allow organizations to adapt quickly to change, whether onboarding new users after an acquisition, rolling out new SaaS platforms, or adjusting to evolving compliance requirements—all without compromising security or user experience.
Challenges of PBAC
Despite its benefits, PBAC is not without challenges. Some common pitfalls to look out for are:
Complexity – Crafting effective policies requires deep collaboration between security, IT, and business teams. Poorly scoped policies can lead to denied access for legitimate users or, worse, drive users toward risky workarounds.
Performance – Real-time policy evaluation at scale can strain system resources, especially as the number of users, devices, and attributes grows. Without proper optimization, this can introduce latency or affect availability.
Adoption and alignment – PBAC is most effective when there’s buy-in across teams. Without alignment between IT, security, and business stakeholders, policies often become fragmented or inconsistently enforced.
Policy sprawl – As organizations grow, overlapping or redundant policies can creep in, making troubleshooting difficult and audits unnecessarily complex.
Testing and rollback – Without simulation and version control, a single policy misconfiguration can cause outages or inadvertently expose sensitive data. Robust testing and rollback procedures are essential for stability and security.
Thoughtful governance, clear documentation, and ongoing maintenance can help mitigate these issues and ensure PBAC scales effectively.
Common use cases of PBAC
PBAC adapts well to industries and environments with complex or evolving access needs:
Healthcare – Enforcing HIPAA restrictions based on user role and patient context.
Finance – Managing access to sensitive data by transaction type or risk level to support SOX or PCI DSS compliance.
Government and defense – Enforcing data classification controls aligned with NIST or ISO frameworks.
Multi-tenant SaaS platforms – Providing delegated admin rights and fine-grained tenant-level access without complex role hierarchies.
Hybrid and cloud environments – Centralizing policy enforcement across diverse systems and apps to minimize friction.
Read more: Customer IAM in Banking: Considerations & Best Practices
Best practices for implementing PBAC
As noted above, PBAC requires attention to detail to implement effectively. These strategies can help organizations avoid common pitfalls while maximizing the value of their investment:
Start with high-impact, high-risk use cases – Pilot PBAC where it can drive the most value, such as protecting administrative interfaces, sensitive databases, or regulated workloads. This allows you to demonstrate ROI early while keeping the scope manageable.
Centralize policy management and governance – Maintain a single source of truth for all policies, with clear ownership and documentation. This ensures consistency across teams, reduces redundancy, and simplifies audits.
Simulate and test policies before deployment – Use staging environments, policy-as-code practices, or built-in simulation tools to validate rules. Testing helps avoid production disruptions and builds confidence in your PBAC system.
Integrate with identity and risk systems – Connect PBAC to existing IAM, governance, and security monitoring platforms to create a unified access and risk management workflow. This integration strengthens visibility and speeds up incident response.
Leverage versioning and rollback – Implement version control for policies to make it easier to track changes, troubleshoot issues, and roll back quickly in case of errors.
Review and update policies regularly – Treat policies as living documents. As your environment changes—new applications, new teams, or new compliance requirements—schedule regular reviews to keep your PBAC framework effective and secure.
Organizations that pair these practices with strong communication and cross-team collaboration are more likely to achieve the dual goals of robust security and smooth user experience.
Set up PBAC with Descope
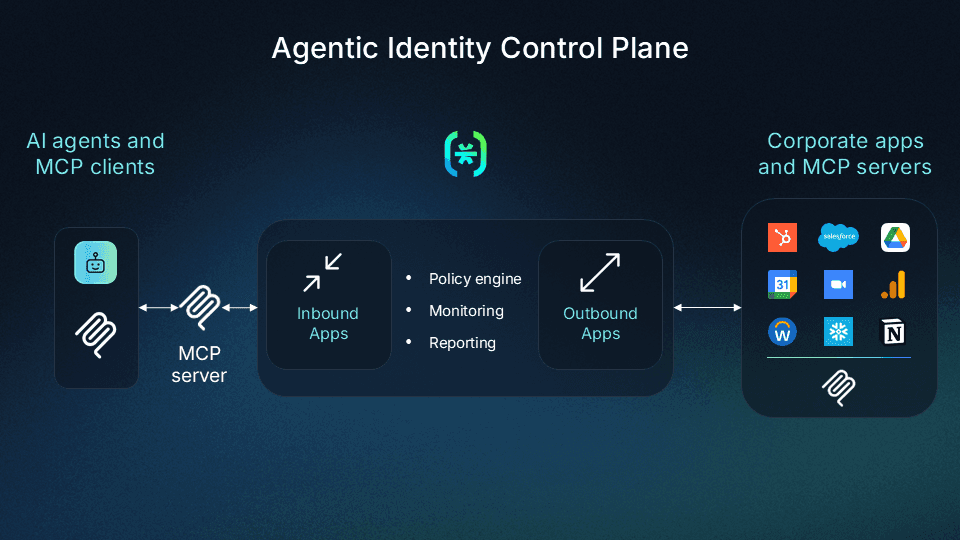
Descope provides a drag & drop platform to help organizations manage identity journeys for end users, business customers, partners, AI agents, and MCP servers. This suite includes out-of-the-box support for RBAC, fine-grained authorization like ReBAC and ABAC, as well as the tools organizations need to implement PBAC.
For organizations wishing to institute policy controls for governing AI agent access to corporate resources, the Descope Agentic Identity Control Plane allows for creating access rules based on user roles, JWT claims, and the veracity of the AI agent requesting access.
To explore easier authorization, sign up for a Descope Free Forever account. Have questions? Book a demo with our team.





