Table of Contents
What is CBUAE Notice 2025/3057?
The United Arab Emirates has become the first country in the world to mandate the complete elimination of SMS and email one-time passwords (OTPs) for consumer-facing financial institutions. But it’s far from the first nation in recognizing these methods are essentially obsolete. The UAE’s decisive action is part of a growing international movement to phase out vulnerable authentication in favor of phishing-resistant alternatives:
In 2024, the Monetary Authority of Singapore (MAS) required retail banks to phase out SMS OTPs for customers who had already enabled digital tokens (while encouraging others to make the switch).
The Philippines' Bangko Sentral issued a directive in early 2025 that ordered banks to “limit the use of authentication mechanisms that can be shared to, or intercepted by, third parties.”
Even the European Union, while not outright banning SMS OTPs under PSD2, has made their use increasingly restrictive and is actively promoting passkeys and other phishing-resistant methods.
And now the CBUAE (Central Bank of the United Arab Emirates) is the latest to join the trend with Notice 2025/3057 issued in May 2025. This directive requires licensed financial institutions to phase out email and SMS OTP-based authentication methods (among many other new policies) by March 31, 2026. The directive comes at a time when digital fraud is at an all-time high. According to the National Financial Ombudsman Scheme, digital banking fraud in rose sharply in early 2025, with a 73% increase in complaints over the previous year.
But unlike other OTP-restricting motions, the CBUAE has created immediate urgency by shifting fraud liability: as of July 2025, financial institutions must fully refund any 3D Secure (3DS) fraud involving SMS OTP. This means the financial exposure began months before the final compliance deadline.
While it’s easy to view Notice 3057 as just another regulatory burden, organizations can leverage this opportunity for competitive advantage. Banks that implement strong, phishing-resistant authentication quickly will reduce fraud losses, lower operating costs, and achieve superior user experiences.
This blog discusses the regulatory expectations after the mandate’s deadline, how financial institutions can comply, and ways to make the most of this new directive.
What is CBUAE Notice 2025/3057?
In May 2025, the Central Bank of the UAE issued Notice CBUAE/FCMCP/2025/3057, a sweeping mandate targeting all consumer-facing financial institutions. The directive represents a paradigm shift in how UAE-licensed banks must protect their customers’ accounts and transactions from fraud.
Key prohibitions
The notice explicitly bans SMS OTP, email OTP, and static passwords as standalone authentication methods. These methods are widely seen as vulnerable to sophisticated attacks like SIM swapping, phishing, man-in-the-middle attacks, and credential stuffing.
OTPs are objectively on the weaker end of the second-factor spectrum—an issue for which Descope has previously sounded the alarm, noting that not all MFA is equal. In fact, we recently helped a large enterprise company recover from an SMS OTP MFA bypass attack where the threat actors used spoofed URLs and fake landing pages to intercept user credentials and SMS OTPs in real-time.
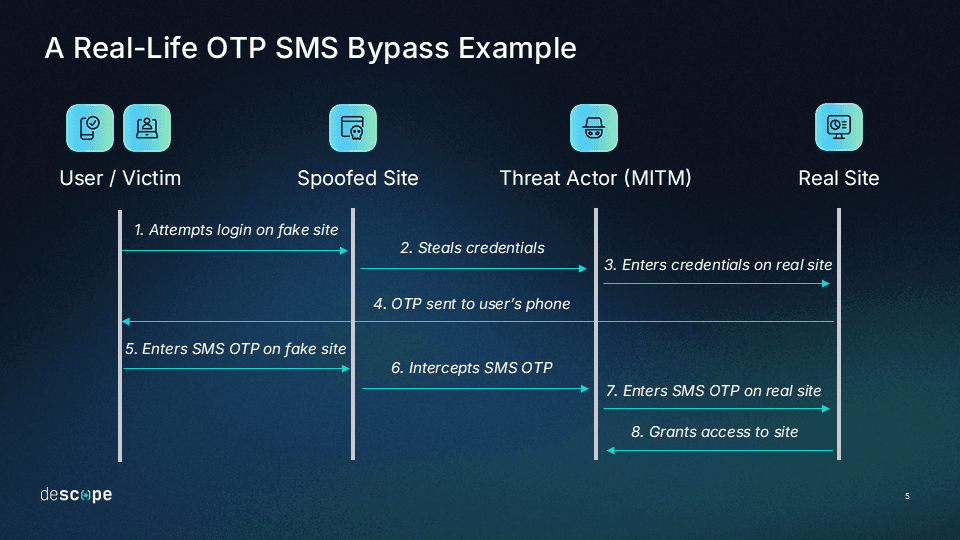
The new prohibitions aim to curb the rising rates of fraud in the UAE. A 2024 GASA (Global Anti-Scam Alliance) report noted that 43% of UAE residents were encountering more scams than in the previous year, with 27% losing money to them. More than half (51%) had received scam messages via SMS, and another 56% had received scams through instant messaging apps (e.g., WhatsApp).
Immediate liability shift
Unlike the March 2026 compliance deadline for full implementation (after which penalties will take effect), one provision is already in place: financial institutions are now liable for any 3D Secure fraud involving SMS OTPs. This means consumer-facing banks must fully refund customers for any such fraud events, creating immediate pressure to move away from SMS-based authentication even before the final deadline.
Required authentication methods
The directive identifies several authentication methods that meet its new standards:
FIDO2 passwordless authentication: Cryptographically secure authentication tied to the user’s device
Biometric authentication: Fingerprint and facial recognition leveraging onboard device capabilities
In-app authentication: Push notifications and secure approvals from within banking apps
Hardware or software tokens: Cryptographic tokens for transaction confirmation
Session protection
Institutions affected by the new mandate must automatically suspend sessions when detecting malware, screen-sharing software, and remote access tools (e.g., Remote Access Trojans, or RATs). These are all common indicators that a customer’s device has been compromised during an active fraud attempt, and the new directive shifts responsibility for uncovering it onto banks.
Real-time fraud detection
Beyond session suspension and authentication, Notice 2057 mandates comprehensive fraud prevention infrastructure: real-time detection systems that analyze every transaction to identify unusual consumer behavior. These systems must be capable of automatically stopping or declining suspicious transactions to prevent fraud attempts.
The directive requires integration of device, location, and behavioral analysis into fraud detection systems. Risk-scoring mechanisms must evaluate the probability of fraudulent activity for each transaction, with detection tools monitoring for patterns like multiple failed logins (velocity), impossible travel patterns or geographic anomalies (geolocation and IP address), and bot-like behavior.
Who must comply, and which teams should implement it?
Notice 3057 applies to all UAE-licensed financial institutions offering consumer-facing services. These include:
Retail banks: Both domestic and international banks serving UAE customers
Card issuers: Credit, debit, and prepaid card providers
Payment service providers: Companies facilitating digital payments and transfers
E-wallet providers: Mobile wallet and stored value facility operators
Digital banking platforms: Neobanks and digital-only financial services
The directive specifically targets financial institutions that serve UAE consumers, aiming to curtail the increasingly prevalent rates of digital fraud over the last several years.
How to shore up auth for 3057 compliance
Meeting the March 2026 deadline, which (at the time of writing) is in a mere five months, requires immediate action. Here’s how organizations can approach compliance both quickly and strategically.
Audit authentication infrastructure, prioritizing 3D Secure
Begin by mapping every point where SMS and email OTPs are currently used across all channels: mobile apps, web banking, call centers, and brick-and-mortar. Prioritize 3D Secure SMS OTP flows first, since fraud liability has already shifted to financial institutions for these types of transactions.
Document gaps in between your existing methods and what Notice 3057 demands: Do you have the proper fraud detection tools in place? Can you automatically end sessions if remote access is uncovered? This audit should serve as the foundation for your implementation roadmap, outlining the scope of what’s required.
Implement FIDO2 passwordless authentication
Notice 3057 specifically calls out FIDO-based authentication as a suitable alternative, making passkeys the most compliance-friendly choice for financial institutions. FIDO2 passkeys are inherently resistant to phishing, and even sophisticated, spoofed sites can’t intercept or steal passkeys. This is because, unlike OTPs, they’re cryptographically bound to your specific site or application and the user’s device.
Passkeys leverage mechanisms consumers are already familiar with, like Apple’s Face ID or a simple fingerprint scan on a smartphone. Because they work seamlessly with existing hardware and don’t require users to learn new processes, they’re the ideal route for meeting 3057 compliance before the deadline.
Deploy risk-based adaptive / step-up authentication
The directive explicitly requires that device, location, and behavioral determiners be integrated into an organization’s fraud detection framework. Implementing a risk-based authentication (RBA) approach allows banks to automatically and dynamically adjust authentication requirements based on the context.
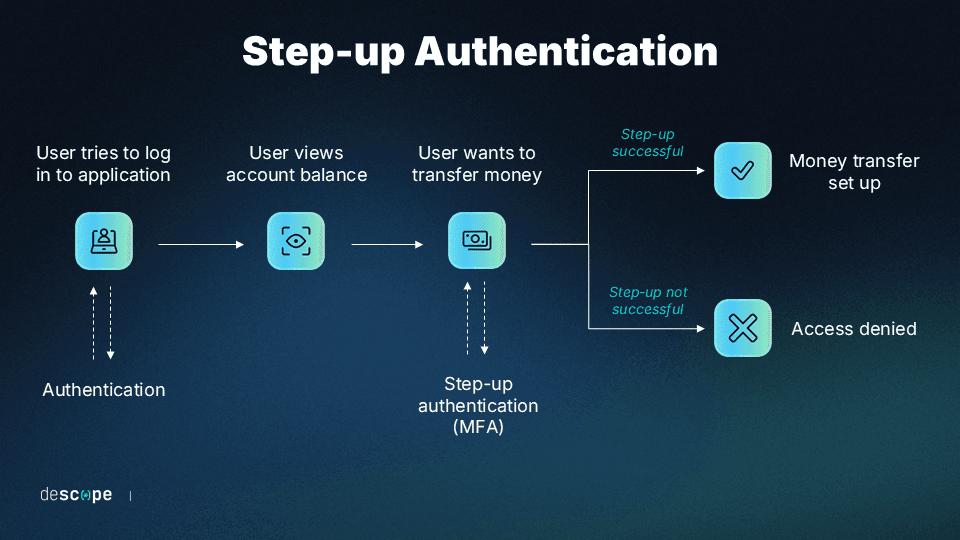
The mandate clearly outlines conditions for high-risk transactions, which should always trigger additional authentication steps (i.e., step-up authentication). However, a low-risk transaction should also be stepped up if it raises risk flags. These could be factors like using a new device, coming from an unfamiliar IP address, or making attempts in quick succession across geographically impossible locations.
Plan a phased customer migration
While the mandate is unavoidable, it’s reasonable to expect some consumer confusion and even pushback. Prepare accordingly by deploying a multichannel communication campaign that explains what’s changing and why. Organizations should emphasize both enhanced security and improved convenience over the now-prohibited methods.
Create visual tutorials and comprehensive FAQs for every new authentication method you plan to adopt. Consider a segment-based rollout that introduces changes gradually. Leverage A / B testing to trial different compliant authentication flows with audience subgroups to identify which approaches minimise friction and yield more successful login rates.
How Descope supports the directive
The Central Bank of the UAE’s directive is more than a compliance exercise. It is a fundamental shift away from legacy authentication methods toward modern, phishing-resistant approaches. For many financial institutions, the biggest challenge will be balancing regulatory urgency with the need to preserve customer trust and reduce friction across everyday banking experiences.
Descope was built to make that transition easier. By implementing our no / low code workflows, passwordless support, and identity orchestration platform, banks and payment providers have the ability to quickly replace methods such as SMS OTP while adopting passkeys, adaptive MFA, and trusted device recognition.
Requirement | How Descope helps |
|---|---|
Weak authentication replacement | Replace SMS/email OTP with TOTP, passkeys, and magic links using no / low code workflow components |
Strong Customer Authentication (SCA) | Enforce two or more factors across all flows with configurable policies |
Biometric support | Native FIDO2 passkey support with streamlined migration paths from legacy systems |
3D Secure compliance | In-app authentication, passkeys, and TOTP alternatives that eliminate SMS OTP liability |
Step-up authentication | Out-of-the-box, configurable step-up for sensitive actions like transfers and account security changes |
Trusted devices | Built-in device fingerprinting, plus risk-based auth for low-risk actions to reduce friction |
Fraud detection integration | Stream authentication logs to anti-fraud tools, and trigger adaptive auth responses based on risk signals |
Data security controls | SOC 2 Type II and ISO 27001-certified with RBAC and fine-grained authorization controls |
Consumer empowerment | Profile widgets enable customer self-service for managing authentication preferences and account security |
Descope offers several key advantages for complying with Notice 3057 quickly: speed of implementation, augmentation for existing infrastructure, and integration with out-of-the-box functionality.
Speed to deployment - Descope’s low-code flows and prebuilt components let banks implement compliant authentication in days and weeks, not months. Teams can configure passwordless login, adaptive MFA, and step-up checks in a visual console, meeting the March 31 deadline without custom development delays. For instance, Navan implemented magic link MFA with Descope in four days.
Augmentation capabilities over complete replacements - Descope overlays modern authentication on existing systems, allowing for gradual migration. Institutions can replace SMS OTP in high-risk flows first, then expand over time, which presents a practical approach for legacy frameworks that are hard to upgrade in production. For instance, Branch Insurance adopted Descope passkeys without changing their existing user store (Amazon Cognito).
Fraud connectors - Descope provides a plug & play ecosystem of third-party connectors that can be embedded into user journeys. Fraud signals from tools such as reCAPTCHA Enterprise, Forter, Fingerprint, and Bitsight TI can enhance organizations’ login risk detection and mitigation capabilities.
Flexibility: Descope’s no / low code nature allows organizations to experiment with different phishing-resistant MFA methods and run A/B tests to determine which method offers the better balance for their users’ security and onboarding expectations.
The clock is ticking on Notice 3057 compliance, and every day with SMS OTP-based 3DS authentication exposes your organization to fraud liability. Descope can help you deliver phishing-resistant authentication in weeks, without requiring a complete reconfiguration of your identity stack.
Schedule a demo to see how UAE financial institutions can meet Notice 3057 requirements with Descope, or start building compliant auth flows now with a Free Forever account.






