Table of Contents
Common passwordless auth methods
Passwordless authentication is redefining how users access applications. By removing passwords, the weakest link in most security systems, it strengthens protection against phishing, credential stuffing, and account takeover while improving user experience. For developers and organizations alike, going passwordless is not just a security enhancement but a strategic shift toward simpler, safer digital experiences.
From consumer-facing apps to large-scale SaaS platforms, authentication plays a vital role in both trust and usability. A well-designed passwordless system can accelerate onboarding, reduce login friction, and lower support costs tied to password resets, all while maintaining compliance and scalability.
In this guide, we explore the top 9 passwordless authentication solutions available today. We outline how passwordless authentication works, its key benefits, and which platforms best fit your business or technical requirements.
Common passwordless auth methods
Passwordless authentication verifies a user’s identity without requiring a password. Instead, it relies on secure factors such as passkeys, biometrics, one-time codes, or magic links that eliminate the risks of stolen, guessed, or reused credentials.
Modern passwordless systems combine several technologies to balance security and convenience:
Passkeys and FIDO2 / WebAuthn: Cryptographic credentials bound to devices that replace passwords with biometric or PIN-based authentication.
Magic links: Email-based one-click sign-ins that skip password entry entirely.
One-time passcodes (OTPs): Temporary verification codes sent via email, SMS, or app notification.
Biometric authentication: Fingerprint, facial recognition, or hardware token verification tied to the user’s device.
OAuth and social logins: Users sign in with existing Google, Apple, or LinkedIn accounts via OAuth 2.0, reducing friction and boosting conversion.
Unlike traditional password-based systems, passwordless authentication removes the most common vector for breaches and user frustration. It delivers a frictionless sign-in flow that is more secure, faster to deploy, and easier for end users to adopt.
The right passwordless platform helps organizations reduce login friction, defend against phishing, meet compliance mandates, and scale across multiple applications or tenants. Below, we compare today’s leading passwordless authentication solutions, highlighting their capabilities, strengths, and ideal use cases.
Also read: 4 Benefits of Passwordless Authentication
With this background in mind, let’s look at the top customer passwordless authentication solutions available today.
Descope
Overview
Descope is a modern identity platform built to make passwordless authentication simple, secure, and adaptable for any external-facing application. Designed for developers and product teams, Descope replaces traditional password-based systems with frictionless login experiences such as passkeys, magic links, one-time passcodes, and social login. Its visual workflow editor and extensive SDK library allow teams to design and deploy custom authentication flows without complex backend code or infrastructure management.
Beyond passwordless login, Descope supports multi-tenant SSO, adaptive MFA, and fine-grained access control across B2C and B2B environments. It provides built-in orchestration tools that let developers connect risk engines, fraud tools, and external identity providers within a single, unified flow. This approach makes it possible to deliver seamless, secure access across all user types, including end customers, business partners, and even AI agents and MCP servers.
Key capabilities
Comprehensive passwordless authentication: Support for passkeys, OTP, magic links,social login, and Google One Tap, giving users multiple secure, frictionless ways to sign in without passwords.
Visual workflow editor: Drag and drop passwordless and MFA flows to design custom login experiences without writing backend code.
Adaptive MFA and security controls: Protect accounts with context-aware MFA, session management, and bot detection that respond dynamically to risk.
Backup auth methods: Add conditional steps to provide backup auth and MFA methods when primary methods fail (e.g. when the end user’s device is not WebAuthn-compatible).
Prebuilt UI widgets: Quickly embed self-service passwordless auth (e.g. adding passkeys and authenticator apps) and account recovery components (e.g. resetting passwords) into any web or mobile app.
SDKs and APIs for modern frameworks: Broad developer coverage across 15+ SDKs, including Next.js, Flutter, React Native, and more.
Connector ecosystem: Integrate seamlessly with third-party tools for risk, fraud, analytics, and directory sync.
Integration-ready orchestration: Enrich user journeys with data and actions from third-party fraud, go-to-market, and compliance tools.
Strengths
End-to-end passwordless experience: Built-in support for passkeys, magic links, OTP, biometrics, and social login enables fully passwordless authentication across web and mobile.
Faster implementation: Visual workflows let teams design and test passwordless flows without backend complexity or infrastructure setup.
Experimentation-friendly: Create A/B tests to randomize traffic between different onboarding paths and auth methods for data-driven and phased rollouts.
Adaptive security: Risk signals trigger additional MFA only when needed, balancing protection with a seamless user experience.
Consistent user experience: Unified passwordless login across devices and channels reduces friction and boosts engagement.
Developer-first design: SDKs, APIs, and embeddable components make it easy to integrate passwordless authentication into any stack.
Scalable for every use case: From consumer apps to multi-tenant SaaS platforms, Descope supports passwordless login for every audience.
Transparent pricing and support: Predictable usage-based pricing and responsive developer assistance for teams of any size.
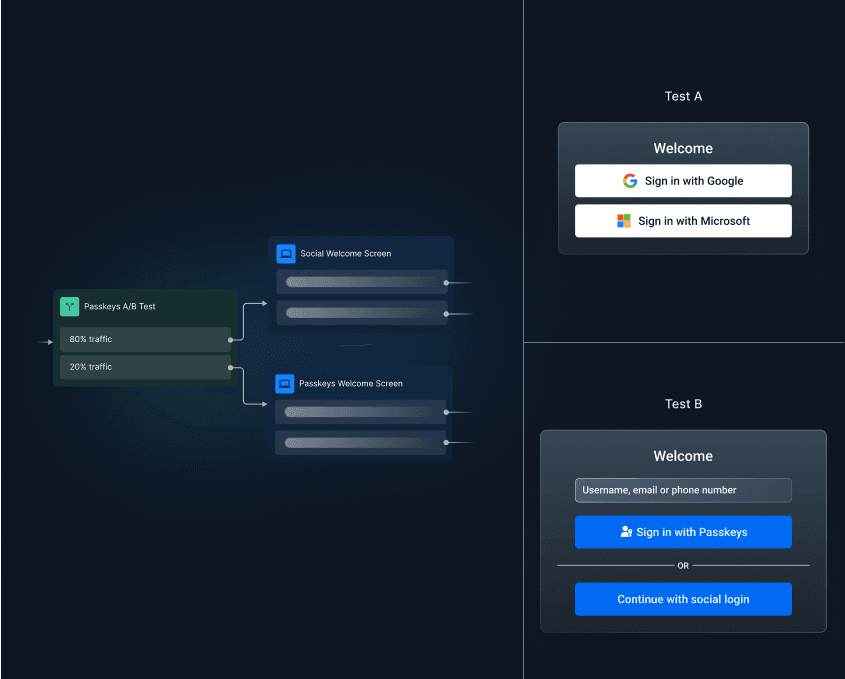
Ideal for
Descope is ideal for developers and product teams building consumer or SaaS applications that need passwordless authentication, multi-tenant SSO, and adaptive MFA without the complexity of managing identity infrastructure. It’s equally suited for startups launching fast and enterprises modernizing legacy systems. With Descope, teams can deploy secure, user-friendly login experiences that scale with their products and customers.
Auth0
Overview
Auth0, part of Okta, is one of the most widely recognized identity platforms offering hosted authentication for web, mobile, and enterprise applications. It provides support for passwordless authentication methods such as WebAuthn passkeys, magic links, and one-time passcodes, along with adaptive MFA and enterprise SSO.
Auth0’s extensibility through Actions, Hooks, and APIs makes it flexible for custom logic and advanced integrations, though setup and maintenance can become complex as projects scale.
Key capabilities
Support for passkeys, WebAuthn, magic links, and one-time passcodes
Hosted login pages with customization and branding options
Adaptive MFA for step-up verification based on risk and context
SSO and federation using SAML, OIDC, and social identity providers
Strengths
Passwordless support: Built-in passkey and WebAuthn options deliver phishing-resistant login experiences.
Enterprise readiness: Supports SSO, directory sync, and advanced access policies for large organizations.
Developer ecosystem: Documentation, SDK coverage, and a large integration marketplace.
Ideal for
Organizations that need enterprise-grade passwordless authentication with broad protocol support and are prepared for the added complexity and tiered pricing.
Amazon Cognito
Overview
Amazon Cognito is AWS’s managed authentication and user management service that provides passwordless and password-based login options for web and mobile applications. It supports FIDO2 and WebAuthn passkeys, one-time passcodes, and integration with major social and enterprise identity providers. Cognito is tightly integrated with the broader AWS ecosystem, making it a natural choice for developers already building on AWS infrastructure.
However, configuration complexity and limited no-code capabilities can make it difficult to scale or customize user experiences.
Key capabilities
Passwordless authentication using FIDO2 and WebAuthn passkeys
One-time passcode (OTP) login and multi-factor authentication support
Identity federation with SAML, OIDC, and social providers
Deep integration with AWS services like API Gateway, AppSync, and IAM
Customizable authentication logic using AWS Lambda triggers
Strengths
AWS ecosystem alignment: Works with other AWS tools and services.
Passwordless options: Native FIDO2 and WebAuthn support enhance login security.
Custom logic through Lambda: Developers can extend and modify authentication flows with serverless functions.
Ideal for
Teams already invested in AWS that want to leverage native passwordless capabilities while keeping authentication close to their infrastructure. For organizations that need more flexibility or visual orchestration,
Descope enhances AWS-native auth with an AWS SaaS Builder Toolkit plugin to add passkeys, adaptive MFA, and drag-and-drop passwordless flows. It can also extend Cognito as an OIDC Provider.
Microsoft Entra External ID
Overview
Microsoft Entra External ID enables organizations to manage both workforce and external identities with strong support for passwordless authentication. Through FIDO2 security keys, Windows Hello for Business, and Microsoft Authenticator app sign-ins, Entra External ID helps enterprises reduce password-related risks while maintaining compliance and governance.
It integrates tightly with Microsoft 365, Azure, and thousands of SaaS applications, making it a common choice for organizations already operating within the Microsoft ecosystem.
Key capabilities
Passwordless login using FIDO2 security keys, Windows Hello, and Microsoft Authenticator
Adaptive access policies that evaluate user, device, and session risk
Lifecycle management with access reviews, provisioning, and audit logging
Conditional Access policies for contextual and risk-based authentication
Strengths
Enterprise-grade passwordless authentication: Native FIDO2 and Windows Hello support deliver secure login experiences.
Comprehensive governance: Built-in tools for audit trails, compliance, and lifecycle management.
Adaptive security: Policies dynamically adjust access based on user behavior and device posture.
Ideal for
Large organizations and regulated industries that need enterprise passwordless authentication integrated with compliance, governance, and access control.
Firebase Authentication
Overview
Firebase Authentication is Google’s developer-focused identity service that simplifies user sign-in for web and mobile apps. It supports passwordless authentication methods such as email link sign-in, one-time passcodes, and Google One Tap.
Built directly into the Firebase platform, it integrates with other Google services like Firestore, Cloud Functions, and Firebase Hosting. While ideal for small teams and mobile-first products, Firebase can become difficult to scale or migrate from as applications grow.
Key capabilities
Passwordless authentication via email link sign-in, OTP, and Google One Tap
Support for social login with Google, Apple, and Facebook
Anonymous sign-in for guest user sessions
Prebuilt UI libraries for web, iOS, and Android applications
Integration with other Firebase services such as Firestore and Cloud Functions
Strengths
Fast setup: Developers can enable passwordless and social login methods.
Mobile-first experience: Optimized for Android, iOS, and cross-platform development.
Seamless ecosystem: Works natively with Firebase and Google Cloud services.
Ideal for
Startups, small teams, and mobile developers looking for simple passwordless authentication that can be launched quickly. Firebase Auth is ideal for projects already using Google Cloud or Firebase, though larger teams may encounter challenges with customization and vendor lock-in as their needs evolve.
Also read: Add Passkeys to Firebase / GCP Identity Using Descope
OneLogin Customer Identity
Overview
OneLogin is an enterprise identity solution that supports both traditional and passwordless authentication methods for employees, customers, and partners. It offers secure access through one-time passcodes, biometric verification, and adaptive MFA, helping organizations reduce reliance on passwords while maintaining strong access controls.
Key capabilities
Passwordless login through biometric verification, OTP, and push notifications
Adaptive MFA with contextual risk analysis and policy enforcement
Centralized SSO across cloud and on-prem applications
Directory sync and automated provisioning for external users
Strengths
Passwordless options: Supports multiple passwordless methods, including biometrics and one-time codes.
Adaptive protection: Analyzes risk signals to determine when additional verification is needed.
Security-focused design: Built to reduce credential theft and unauthorized access.
Ideal for
Mid-market and enterprise organizations that want to adopt passwordless and adaptive authentication without rebuilding their existing infrastructure. OneLogin is well-suited for teams prioritizing access across mixed cloud and on-prem environments.
Keycloak
Overview
Keycloak is an open-source identity and access management solution originally developed by Red Hat that gives organizations full control over their authentication stack. It supports passwordless authentication through FIDO2 and WebAuthn, allowing users to sign in securely with device-bound credentials or biometrics instead of passwords.
Because it is self-hosted, Keycloak offers maximum flexibility and customization, though it also introduces operational overhead, upgrade challenges, and scaling complexity as deployments grow.
Key capabilities
Passwordless authentication using FIDO2 and WebAuthn
Support for OIDC, SAML, and LDAP for broad interoperability
Customizable login pages and authentication flows
Built-in admin console for managing users, roles, and realms
Strengths
Full customization: Control every aspect of passwordless authentication and authorization.
Open-source flexibility: No licensing costs and freedom to modify source code.
Protocol coverage: Supports enterprise standards such as SAML, OIDC, and LDAP.
Ideal for
Organizations with strong DevOps resources that want to self-host passwordless authentication and maintain complete control over configuration and data. Keycloak is best suited for enterprises or government environments that prioritize flexibility and compliance but can manage the added complexity of updates, scaling, and maintenance.
Supabase
Overview
Supabase Auth is the authentication service built into the open-source Supabase platform. It provides developers with lightweight, passwordless authentication options such as magic links, one-time passcodes, and social login, all backed by a secure Postgres database.
Supabase offers a Firebase-like developer experience with open-source transparency and flexible deployment options, making it an appealing choice for startups and teams that want more control over their data.
Key capabilities
Passwordless authentication via magic links and one-time passcodes (OTP)
Support for social login providers such as Google, GitHub, and Apple
Postgres-based user management with row-level security for granular access control
Serverless edge functions for extending authentication logic
Strengths
Open-source flexibility: Full transparency and the ability to self-host without vendor lock-in.
Built-in passwordless methods: Magic links and OTPs make login simple for users and easy to implement.
Postgres integration: Tight coupling with Postgres allows fine-grained authorization and data control.
Ideal for
Developers and startups looking for open-source passwordless authentication with direct database integration. For teams seeking advanced features such as multi-tenant SSO, adaptive MFA, or FIDO2 passkey support, Descope can integrate directly with Supabase to expand authentication capabilities without re-platforming.
Also read: Add Passkeys to Supabase With Descope
HYPR
Overview
HYPR is an enterprise-grade passwordless authentication platform focused on eliminating shared secrets and preventing credential-based attacks. Its HYPR Authenticate solution replaces passwords with FIDO2-certified, phishing-resistant authentication powered by public-key cryptography.
HYPR’s decentralized architecture stores private keys on the user’s device rather than in a centralized server, minimizing the attack surface and reducing the risk of credential theft. It is built for large organizations that need high assurance, regulatory compliance, and seamless user experiences across workforce, customer, and partner access.
Key capabilities
Passwordless authentication using FIDO2-certified cryptographic credentials
HYPR Authenticate app for secure biometric or PIN-based login across devices
Decentralized identity model that keeps private keys on user devices
Multi-factor authentication (MFA) without passwords or shared secrets
Strengths
Phishing-resistant authentication: Private keys never leave the device, protecting against replay and credential attacks.
Decentralized security: Eliminates password databases and reduces breach risk.
Enterprise integrations: Works with major IAM platforms and SSO providers.
Ideal for
Enterprises and regulated industries that require phishing-resistant passwordless authentication with full compliance and strong assurance. HYPR is best suited for organizations prioritizing security, scalability, and risk reduction over rapid developer customization.
Conclusion
Modern passwordless authentication is no longer just a security upgrade. It is a defining factor in user experience and trust. The right solution removes the friction of passwords, stops phishing before it starts, and creates faster, safer sign-ins across every channel. Whether your goals are improving conversion, reducing account takeover risk, or aligning with FIDO2 standards, choosing a flexible and scalable passwordless platform is essential.
Among the available options, Descope stands out for its complete passwordless authentication offering that includes passkeys, magic links, OTPs, and adaptive MFA, all built on a visual workflow editor that removes development complexity. By combining developer-friendly orchestration with enterprise-grade security, Descope helps organizations deliver frictionless, phishing-resistant login experiences that keep users secure and engaged.
For a deeper look at how Descope simplifies passwordless authentication, check out our docs. If you'd like a demo, meet with our auth experts. Also, if you want to try Descope yourself, sign up for a Free Forever Account and start your passwordless auth journey today!






