Table of Contents
What is smishing?
Cybercriminals no longer rely only on email to launch phishing attacks. With text messaging now a primary way people interact with businesses, attackers have shifted their focus to SMS, turning a trusted communication channel into a powerful weapon. Smishing doesn’t just put individuals at risk; it creates openings for account takeover, supply chain disruption, and brand damage.
Understanding how smishing works and why traditional defenses aren’t enough is the first step toward building stronger safeguards.
Main points
Smishing exploits trust in SMS – Attackers use text messages to trick people into clicking malicious links or sharing credentials, making it harder to detect than traditional phishing.
The risk extends beyond employees – Customers, partners, and supply chains can all be compromised, leading to financial losses, regulatory penalties, and reputational damage.
SMS-based auth is a prime target – Fraudulent OTP prompts are a common tactic, which is why organizations should move away from SMS authentication.
Passwordless is the strongest defense – Passkeys, magic links, and authenticator apps remove SMS from the equation, protecting against smishing while improving user experience.
What is smishing?
Smishing is a form of social engineering. The name is a portmanteau combining an abbreviation for “short message service” (SMS) with “phishing.” Like other forms of social engineering and phishing in particular, smishing intends to exploit human vulnerabilities and solicit sensitive information either directly or indirectly by tricking people into unknowingly giving it up.
SMS is an attractive channel for cybercrime because it’s one of the most widely used text messaging platforms in the world. It’s fast and has nearly unparalleled reach, since users generally trust the text messages they receive. That makes it an ideal vehicle for stealing credentials, which remain the #1 battleground for cybercrime in 2025 per Verizon.
On a personal level, smishing can lead to identity theft and direct financial losses, not to mention the difficulty of recovering accounts and/or re-configuring new online personas.
The organizational impact of smishing also cannot be overlooked, as it can lead to system compromise from within that is difficult to detect. If attackers successfully steal users’ credentials, they can access systems without being detected—often until it’s too late.
Smishing vs. phishing
While smishing is a form of phishing, there are some critical distinctions from the broader category that are worth keeping in mind. To begin with, phishing as a whole refers to any cybercrime attack where individuals are lured into providing sensitive information with a fraudulent premise. This includes many different platforms and approaches, including SMS.
However, traditional phishing attacks are launched via email. They are also often high-volume, with minimal customization in many cases. However, some forms of phishing involve significant effort and customization.
For example, spear phishing attacks are targeted toward smaller groups and sometimes even particular individuals. In contrast with traditional phishing, they are extremely high quality and may not include common tells.
Smishing most often occurs over SMS, but attackers increasingly use MMS and app-based SMS gateways as well. Still, SMS remains the standard term and the primary channel. Smishing attackers may opt for the high-volume approach, or they may instead choose highly customized messages. In any case, the reasons these campaigns are so dangerous is that they leverage an accessible, high-trust infrastructure. They’re easy to launch, and open rates tip the scales in the attackers’ favor.
Read more: What Is Broken Authentication and How to Prevent It
Why and how smishing works
Simply put, smishing works because texting is one of the most seamless communication channels in existence. SMS consistently sees extremely high open rates, often reported above 90%, along with relatively low cost per click (CPC) and streamlined analytics, making it an excellent attack vector for cybercriminals. But that’s why it works.
In terms of how it works, the basic chain of events is as follows:
An attacker sends a convincing text to an unsuspecting victim.
The victim clicks on a link in the text, downloads a file, or replies.
Sensitive data is stolen or malware is installed on the target device.
Most often, the thing that makes these messages trustworthy to victims is a social engineering ruse. Attackers may exploit authority, posing as a bank, government official, or executive. They may also instill a sense of panic with texts like “your account will be locked unless you reply.”
This simple process can lead to account takeover, where the victim in question and other entities in their orbit lose exclusive control over one or more of their accounts. If the victim was targeted via a number or device connected to their employer, the attackers could easily obtain credentials and other information that would normally be protected via the user’s account.
Another contributing factor to how smishing works is the lack of widespread SMS protection and monitoring, especially relative to other platforms like Gmail or messengers like Slack.
Common smishing scenarios
Smishing is used in a wide variety of contexts. For example, in 2022 the FBI’s Internet Crime Complaint Center (IC3) issued a public alert after attackers sent large-scale smishing texts impersonating U.S. government officials. This campaign was dangerous enough to trigger a nationwide warning, but many other smishing attacks fly under the radar.
The most common smishing attacks often fly under the radar, with scenarios like:
Fake delivery or service notifications sent to customers in the company’s name
Texts impersonating banks, retailers, or healthcare providers and asking for login info
SMS-based scams asking employees, vendors, or partners for proprietary information
Fraudulent multi-factor authentication (MFA) prompts intended to intercept credentials
Smishing schemes target vulnerabilities closer to home than more traditional phishing. While many people are on the lookout for fraudulent emails, their guard may be down, or at least more relaxed, when it comes to text messages they receive, especially on personal devices.
These situations can be damaging to both the parties impersonated and the individuals and organizations targeted. Beyond financial fraud, smishing can damage brand trust, disrupt supply chains, and expose sensitive partner or customer data, leading to regulatory penalties and reputational harm.
How to defend against smishing
Defending against smishing requires a layered strategy that protects both external stakeholders and internal users. Because the attack surface spans customers, employees, partners, and vendors, organizations need a mix of preventive controls, resilient authentication, and ongoing education.
Strengthen authentication with passwordless
The most effective way to neutralize smishing’s impact is to remove its primary target: credentials and SMS-based one-time passwords (OTPs). Passwordless authentication eliminates the weak links that attackers exploit in text-based phishing.
No SMS codes to intercept: If MFA doesn’t rely on OTPs sent via text, smishing campaigns that try to trick users into sharing them become irrelevant.
Resistance to credential replay: Passwordless methods often use public-key cryptography, so even if an attacker intercepts traffic, they cannot reuse it.
Better user experience: Passwordless flows reduce friction compared to juggling complex passwords and SMS codes, driving both stronger adoption and fewer support tickets.
Organizations rolling out passwordless should prioritize FIDO2/WebAuthn standards, since they work across major browsers and mobile platforms, and allow support for scalable solutions like passkeys.
Replace SMS-based authentication wherever possible
Even if passwords remain part of your stack for now, replacing SMS authentication with app-based authentication (e.g., Microsoft Authenticator, Google Authenticator) dramatically reduces smishing risk. This method ties authentication to devices or cryptographic secrets that can’t be spoofed with a simple text message.
Deploy mobile-first security controls
Because smishing primarily targets mobile devices, organizations should enforce policies and protections at that layer:
Mobile Threat Defense (MTD): Detect and block malicious links, fake profiles, or rogue apps on employee devices.
Domain and SMS filtering: Block known malicious senders or spoofed domains at the carrier or endpoint level.
Mobile device management (MDM): Enforce patching, encryption, and secure app installations to reduce exposure.
Build customer-facing trust signals
External smishing campaigns often impersonate legitimate brands. Companies can lower that risk by:
Using verified SMS and branded sender IDs so customers know when a message is genuine.
Publishing and repeating clear policies like “We will never ask for your password or MFA code via unsolicited emails, texts, or phone calls.”
Running customer education campaigns during high-risk periods (tax season, holiday shopping) when smishing spikes.
Train and empower employees
Finally, technical defenses only go so far without human vigilance. Employee awareness training should go beyond “spot the suspicious text” to cover:
How to report suspected smishing attempts quickly, not just delete them.
Why SMS codes should never be shared outside secure login flows.
How attackers may use smishing to pivot into supply chain or partner ecosystems.
Prevent smishing with smart auth flows
Smishing thrives on one thing: exploiting human trust in text messages to steal credentials and bypass weak authentication. The most powerful way to stop it is to remove the target altogether. By moving beyond SMS-based authentication and adopting passwordless, organizations can protect employees, partners, and customers while delivering a login experience that’s both secure and seamless.
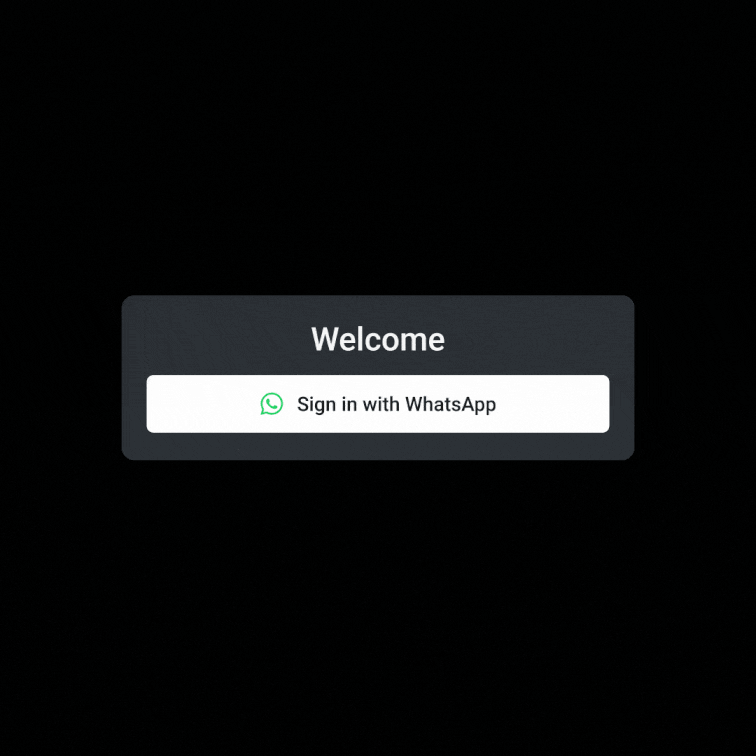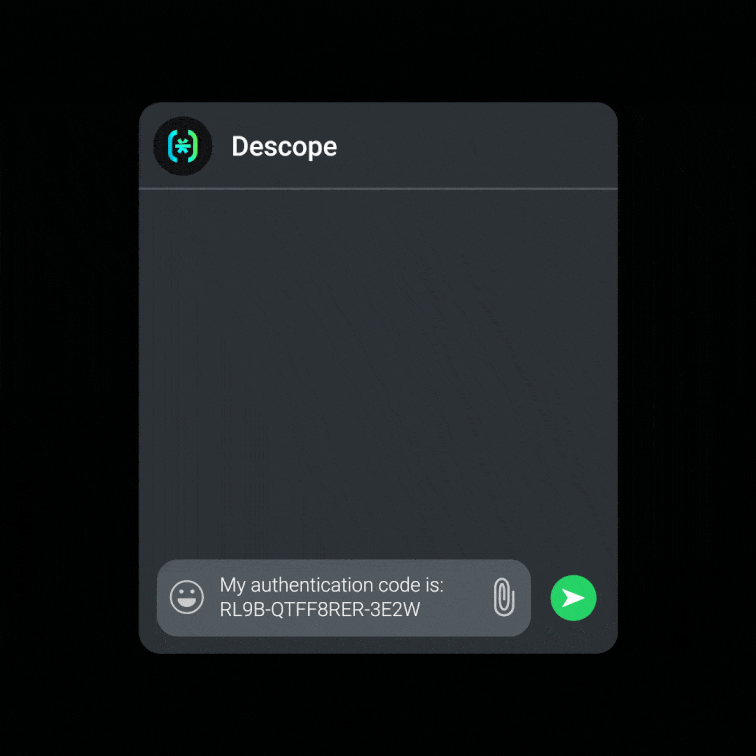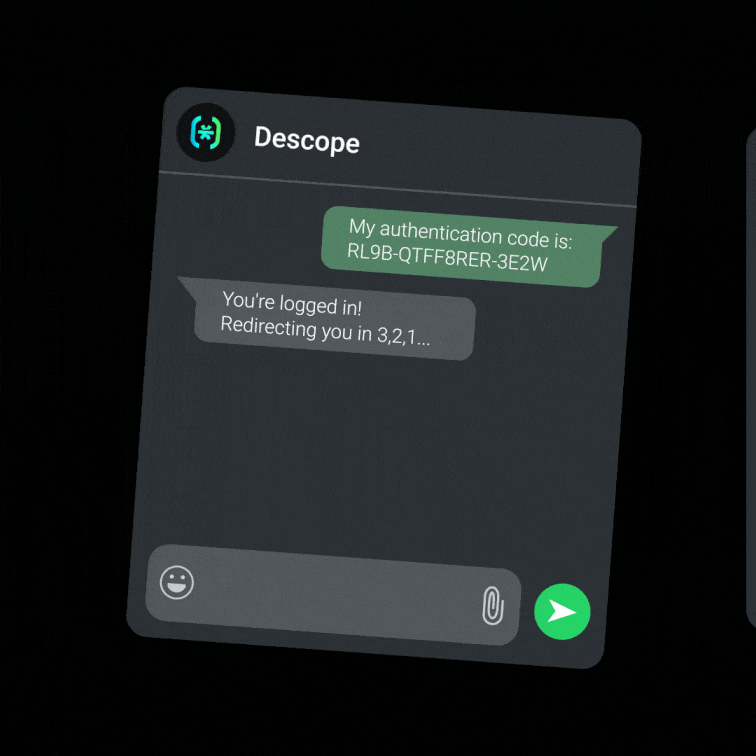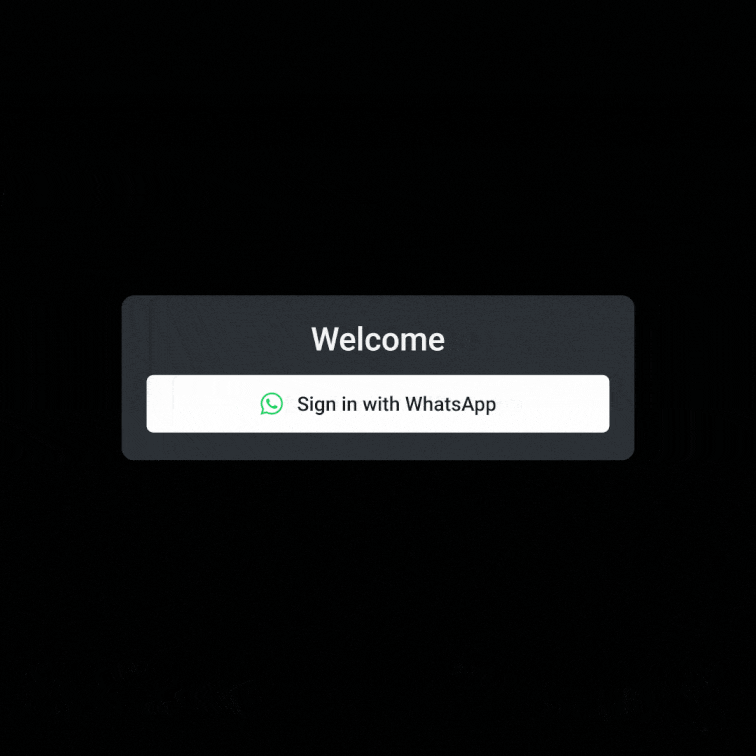
Descope makes that transition simple. Our drag & drop CIAM platform lets you add passkeys, magic links, authenticator apps, and other methods without writing custom code. For organizations in countries where WhatsApp is popular, Descope's nOTP authentication method provides frictionless, one-click authentication via WhatsApp without the user ever having to type in a code.
Sign up for a Free Forever account with Descope to start your smishing-free journey. Have questions? Book time with our experts!