Table of Contents
DORA’s five pillars (and where authentication matters most)
DORA (the Digital Operational Resilience Act) has been fully enforceable since January 17, 2025. At this point in DORA’s lifecycle, you have likely already begun (or, ideally, completed) your compliance journey. If not, you’re probably urgently aware that non-compliance carries penalties up to 2% of daily global turnover for up to six months.
For insurers and financial institutions in the European Union, DORA’s risk management pillars present clear expectations: implement strong cybersecurity, especially authentication, both internally and among your third-party partners. Whether it’s retail banking portals, trading platforms, payment gateways, or insurance claim systems, all need consistent security controls across every touchpoint—inside and out.
Strong authentication directly reduces the likelihood of a customer-facing information and communications technology (ICT) incident. But many organizations still rely on legacy implementations to meet DORA requirements, which either create excessive friction or fail to protect against modern threat vectors like man-in-the-middle (MITM) attacks.
This guide cuts though DORA’s broad challenges to focus on what matters most for authentication and identity security. We’ll show you:
How modern customer authentication capabilities map to specific DORA requirements
Ways to implement them without disrupting customers
Why some DORA-compliant changes can also elevate your user experience
DORA’s five pillars (and where authentication matters most)
DORA aims to build operational resilience through five pillars, each with varying weight for customer identity and access management. Even if you’ve already met DORA requirements, you’ll still need to continue validating compliance both internally and externally. Like all regulations affecting financial institutions and insurance providers, DORA is a constant, ongoing responsibility.
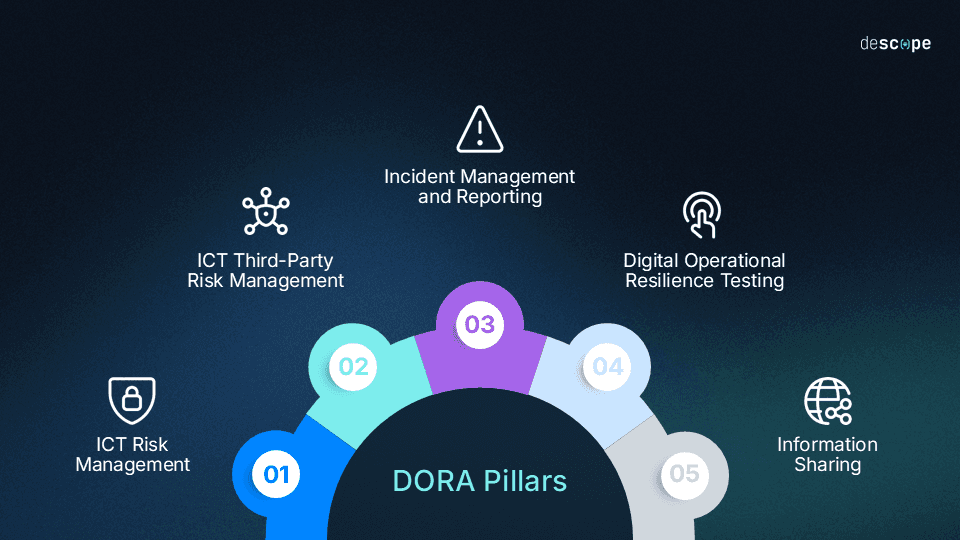
ICT Risk Management establishes governance and controls to prevent, detect, and respond to ICT risks. Requirements include identifying and classifying critical ICT assets, continuous vulnerability monitoring, and annual testing of business continuity plans.
For authentication, this means implementing controls that can identify anomalous access patterns, enforce consistent policies across all systems, and maintain detailed audit trails for incident investigation.
ICT Third-Party Risk Management requires comprehensive oversight of external service providers, particularly those deemed critical. Organizations must maintain a complete register of outsourced activities, monitor concentration risks, and standardize contractual provisions including audit rights and data location transparency.
These obligations extend to authentication services, identity providers, and any third-party systems that handle user credentials or access decisions.
Incident Management and Reporting mandates formal procedures for detecting, classifying, and reporting ICT incidents within strict timelines. Major incidents require initial notification within 4 hours, intermediate reports within 72 hours, and final reports within one month.
Should your organization experience a security event affecting customer identity, it’s vital that your systems generate the audit trails needed to accurately assess unauthorized access attempts. These logs can provide the forensic detail regulators expect in incident reports.
Digital Operational Resilience Testing requires annual testing of ICT systems, with Threat-Led Penetration Testing (TLPT) for critical functions at least every three years. For this pillar, authentication systems will face particular scrutiny. Testers will validate your security by attempting to gain unauthorized access using methods like phishing, credential stuffing, session hijacking, MFA bypass, and other types of social engineering.
Information Sharing encourages the voluntary sharing of threat intelligence with peers and authorities. While less prescriptive than other pillars, this includes sharing indicators of compromised credentials, emerging phishing vulnerabilities, and authentication bypass techniques observed in your environment.
Here’s the key insight for these five pillars: Strong authentication cuts across DORA’s directives as a consistent means for attaining and maintaining compliance. When properly implemented, authentication doesn’t just satisfy DORA’s requirement for internal and third-party ICT risk management; it also provides the logging, threat identification, and resilience against test scenarios to help you meet the rest.
Why DORA can impact UX for better or worse
Meeting DORA isn’t a one-time compliance checkbox you can tick and forget. Financial services customers have become increasingly intolerant of security breaches (and the subsequent security “theater” that they have to wade through in its wake). They’ll abandon transactions, switch providers, or find workarounds when authentication becomes a friction-filled burden.
Some organizations affected by DORA may have chosen to simply tighten their grip on security, but at a significant cost to friction and user experience. This unilateral approach might satisfy a flat reading of the regulations, but you still need to maintain compliance while managing customer expectations.
Instead of implementing rigid controls stemming from a boilerplate interpretation of DORA’s directives, you can tailor authentication journeys to be flexible and contextual. Modern authentication doesn’t mean choosing between compliance and experience, but actually offers the tools to deliver more of both at once.
The banks, insurers, and trading platforms that win post-DORA won’t be the ones with the least thoughtful controls. They’ll be those who implement customer-centric (and compliant) access management that users barely notice. This means moving beyond box-ticking and into solutions that can scale security based on your organization’s unique needs and customer expectations.
Descope capabilities for DORA compliance
While DORA’s scope extends far beyond authentication, identity security forms a crucial component of ICT risk management. With the foundation that DORA compliance should enhance rather than hinder user experience, here’s a breakdown of the specific ways that Descope can help you deliver both security and seamless usability:
Adaptive and step-up authentication
Your organization almost certainly already has some form of multi-factor authentication (MFA) protecting user accounts, since this has been required by PSD2 SCA since 2019. With DORA now in effect, it’s doubly important to enforce MFA to meet the high bar for managing ICT risk.
However, in the case of always-on MFA, customers are challenged with additional security steps every time they log in. While this can raise security posture, it has the added side effect of irritating users.
Step-up authentication only triggers when the customer takes specific actions, such as:
Attempting to change security settings
Requesting a large transfer
Viewing full account and routing numbers
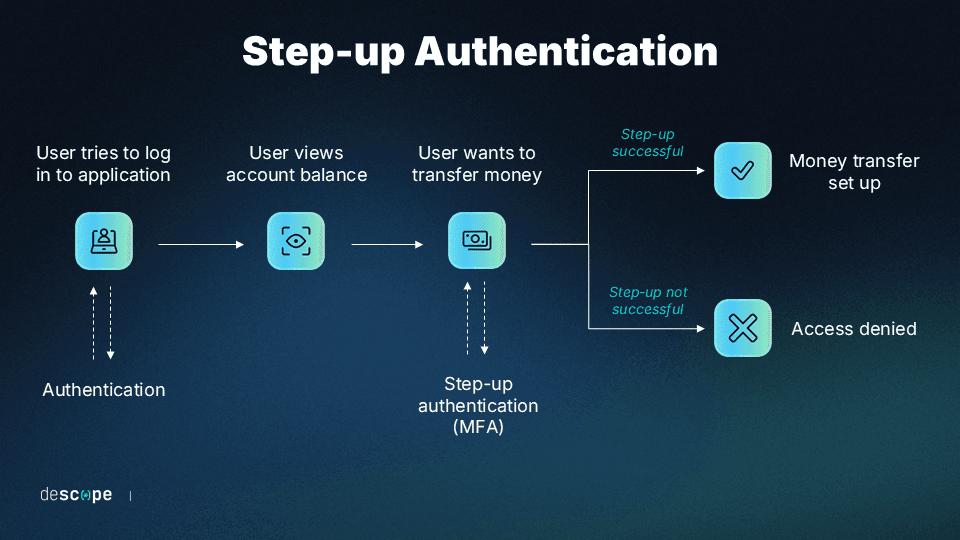
Adaptive MFA (or adaptive authentication) applies additional challenges based on risk signals rather than rigid policies. These signals include:
When previous device fingerprints don’t match the device attempting login
If an unfamiliar IP (or one with a bad reputation, such as a VPN) attempts to log in
When impossible travel appears to happen, in which multiple logins occur in succession from geographically unfeasible locations
The risk-based environment offered by Descope allows organizations to consolidate threat intelligence from multiple sources that you can stack modularly, such as device fingerprinting through Fingerprint, fraud scoring via Forter, IP reputation databases like AbuseIPDB, and behavioral analytics from Google reCAPTCHA Enterprise.
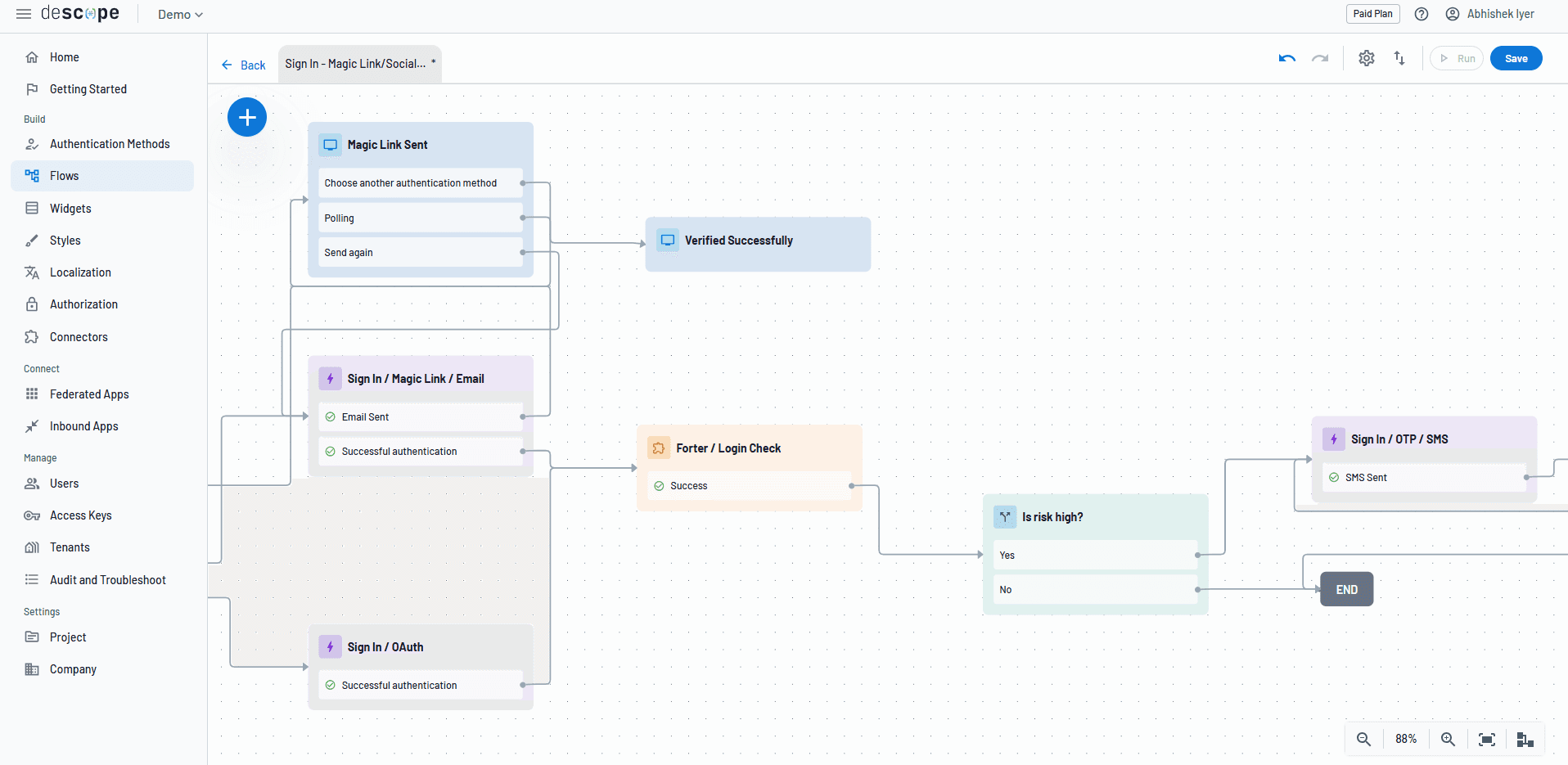
Phishing-resistant MFA
SMS and email one-time passwords (OTPs) are so widely regarded as vulnerable that multiple nations’ banking authorities have begun phasing them out. While DORA doesn’t demand the complete elimination of these methods, they’re widely regarded as less secure (and more likely to land you in the crosshairs of DORA-enforcing regulators).
Descope makes it easy to add methods such as TOTP authenticators, magic links locked to specific browsers or devices, and passkeys that cryptographically prevent phishing attempts. Passkeys, in particular, are well-suited to the mobile experience, where biometric authentication already feels native and natural.
Omnichannel authentication experience
Descope provides workflow-based building blocks to help unify identity flows across web and mobile apps, with native mobile flows that avoid jarring redirects. Customers expect one unified identity across all access points, including subchannels and partners.
For financial services affected by DORA, this can be a critical differentiator. Take insurance as an example: Customers might rarely access your main portal to view a policy, but when they do—whether through the home insurance-focused app or the every-policy website—the experience needs to be consistent even if those applications run discrete systems with separate products.
Strong reinforcement for legacy authentication
Not everyone is ready to abandon passwords entirely. But you can still strengthen password-based authentication significantly by pairing it with phishing-resistant MFA and blocking previously breached passwords. Descope’s Have I Been Pwned integration blocks credentials exposed in known data breaches, preventing compromised passwords from entering your system before they become a DORA compliance incident.
Descope’s built-in bot protection also protects against common password-targeting, automated attacks: credential stuffing, brute force, and password spraying attempts. These safeguards help you make existing authentication methods as secure as possible while you gradually transition to modern alternatives.
Admin controls and audit trails
Descope logs creation, edits, deletion, and login of users, including the authentication method, flow, and much more. Descope auditing captures everything from device info and IP address to the country of origin and the specific auth action performed—which are exactly the forensic details DORA’s incident reporting requirements demand.
For DORA’s ICT risk management pillars (both internal and third-party), these capabilities provide continuous monitoring and the ability to reconstruct any authentication event. When regulators ask about a specific incident, you have the total context.
Flows and A / B testing
Descope’s visual workflow editor, Descope Flows, makes auth changes a matter of drag and drop without any custom code or redeploying your app. This is especially useful for balancing user experience with DORA compliance, thanks to A / B testing capabilities.
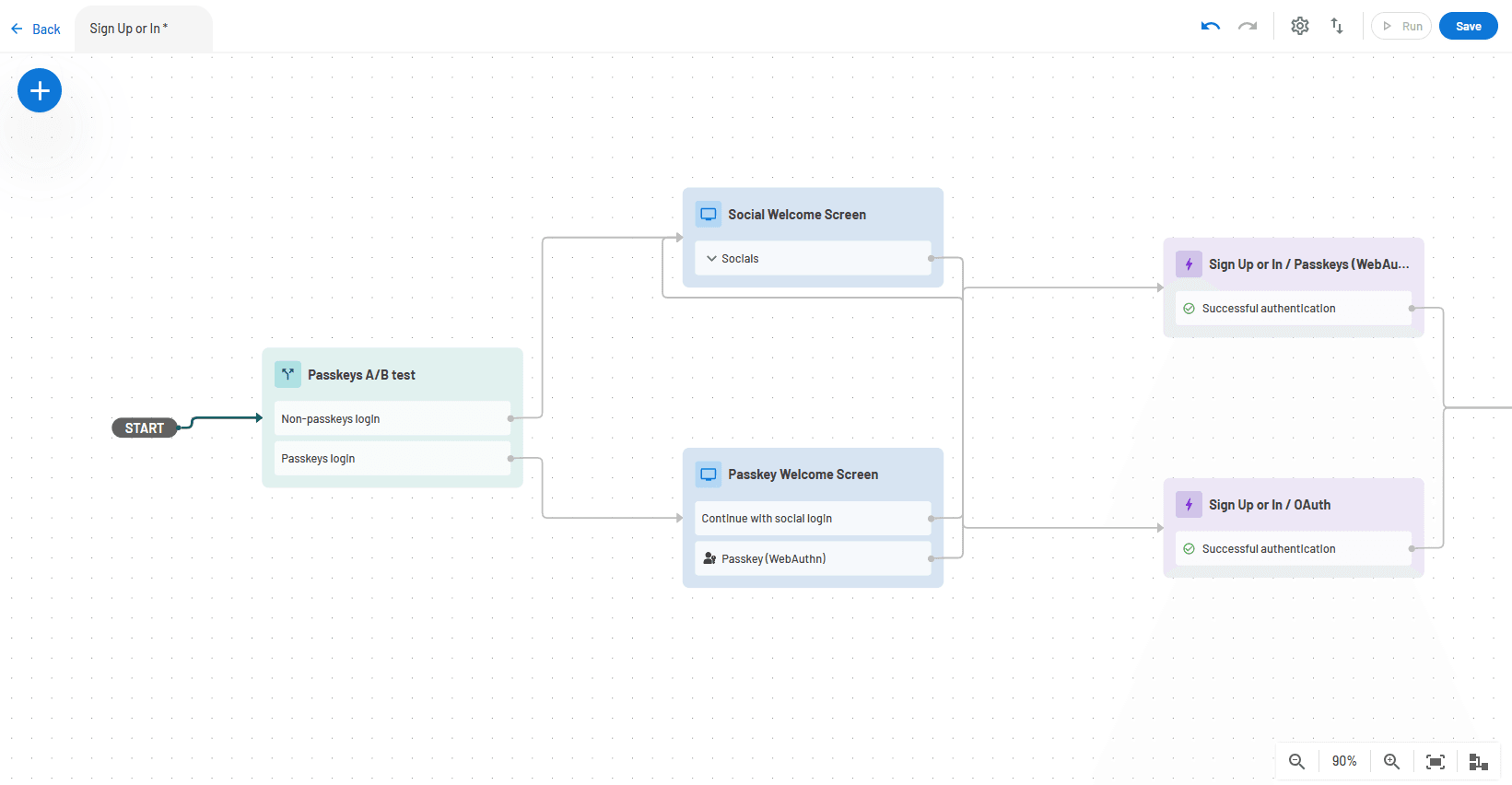
Want to introduce DORA-compliant passkeys to a segment of users currently on passwords? Create a conditional step in your flow using a variable to split traffic: Send 80% of them to your existing login, and 20% to a passkey-enabled version (complete with fallbacks). Descope’s analytics dashboard lets you measure login success rates for each auth method.
Also read: How Branch reduced auth-related support tickets by 50% with Descope passkeys
Staying compliant with DORA while boosting UX
DORA compliance doesn’t have to mean choosing between strong security and seamless user experience. By deploying an intelligent solution tailored to your actual risk, your organization can meet (and exceed) DORA directives while improving customer satisfaction.
With Descope, you can:
Maintain compliance readiness using strong, phishing-resistant authentication and reinforcement for legacy methods
Reduce fraud and account takeover risk with consolidated risk signals, breached password detection, and bot protection
Demonstrate internal and external compliance with comprehensive audit trails and secure integration with third-party systems
Unify customer identity across all channels, creating a single source of truth and a streamlined experience for users
Ready to meet DORA requirements without compromising customer experience? Descope makes it easy to deliver DORA-compliant authentication while maintaining the seamless journeys your users crave.
Sign up for a Free Forever account to start building your first flows, or book a demo with our team to discuss your specific DORA compliance needs.