Table of Contents
MCP and A2A: connect vs. orchestrate
Modern agentic AI systems face two fundamental challenges to become production-viable: enabling tool access and facilitating agent collaboration. While the Model Context Protocol (MCP) and Agent2Agent (A2A) protocol have begun to standardize these interactions, they handle authentication and authorization with distinctly different approaches.
This distinction, however, is by design: Each protocol serves a specific purpose, and the auth modalities they use reflect this.
Whether you’re starting with an agent builder like CrewAI, a framework like LangGraph, or by assembling an MCP server, understanding how these protocols handle authentication is crucial for deploying production-ready agents at scale.
This article covers:
The key distinction in purpose and methodology between MCP and A2A (and why their auth is different)
Each protocol’s auth approach
Best practices for implementing each protocol with auth (or both together)
MCP and A2A: connect vs. orchestrate
Before diving straight into the auth specifics, you’ll want to understand the design philosophy behind each of these protocols. While they absolutely synergize, they’re also built to operate at different levels, at separate (but complementary) layers.
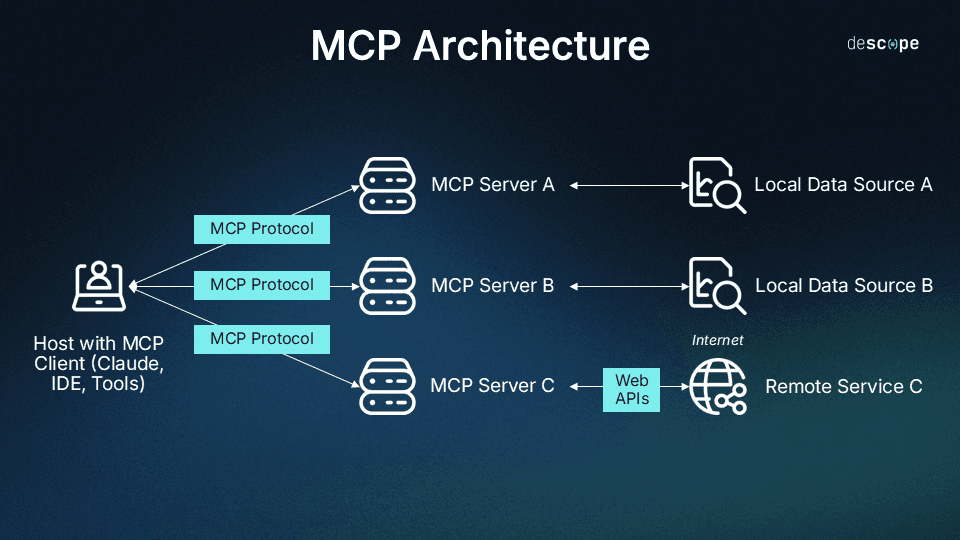
MCP connects models to tools
MCP is all about connecting AI models with external data and tools. It’s based on a client-to-server architecture where a user accesses the client, the client connects to the server, and the server provides the tools or data. While a single client can connect to many different servers, the interactions remain opaque, meaning there’s no shared internal state between them.
A2A connects across ecosystems
A2A’s purpose is right in the name: “agent to agent.” It allows agentic AI systems to communicate with each other, particularly across different frameworks like LangGraph, CrewAI, LlamaIndex, and others. Rather than operating in isolation, agents work together in one runtime with shared context, memory, and authentication parameters.

Different layers, different use cases
Consider that MCP is the emerging standard for LLMs connecting to data and tools, while A2A enables agents (which are typically models equipped with external information or tooling) to collaborate in natural modalities. A2A doesn’t replace existing framework tools; instead, it adds standardized connectivity. These protocols operate at different layers, which is why they have different authentication requirements.
Also Read: MCP vs A2A
MCP authentication: OAuth 2.1 by the book
MCP takes a strict approach to security by mandating OAuth 2.1 with PKCE (Proof of Key for Code Exchange) required for all clients. The protocol's authorization specification mandates full implementation of Authorization Server Metadata (ASM), Protected Resource Metadata (PRM), and Dynamic Client Registration (DCR)—the last of which is expected to be replaced by a new default method, Client ID Metadata Documents (CIMD).
The goal of enforcing these parameters is simple: every MCP deployment should speak the same auth language. Tool access involves sensitive data and actions: databases, APIs, various critical systems. OAuth is already mature and provides auditable, enterprise-proven security. PKCE specifically protects against code interception, which is critical for public clients, while scope-based permissions enable fine-grained access control (FGA).
Key considerations for MCP auth
It’s important to note, however, that the MCP auth spec and OAuth 2.1 are still under active development. For MCP, changes are more frequent than more established protocols; for example, the first iteration of the spec positioned MCP servers as both authorization and resource servers, but recent revisions have separated those roles. Meanwhile, OAuth 2.1 hasn’t been officially published yet and remains in its draft stage.
MCP’s approach provides consistency and opens the door to enterprise-ready security. However, it requires OAuth expertise or reliance on outside experts. PKCE and DCR/CIMD add complexity and overhead that are somewhat niche outside of specialized security fields. And while mandatory compliance with OAuth 2.1 offers standardized security, it also means everyone has to get on board with OAuth to use it.
From a best practices perspective, it’s generally better to use an established OAuth solution rather than building niche security components from scratch.
A2A authentication: flexible by design
A2A takes a fundamentally different approach. Rather than mandating specific auth frameworks, it focuses on declaring and validating them. AgentCards (the main building blocks of A2A) advertise supported schemes like Bearer tokens, Basic Auth, API keys, OAuth, and mutual TLS. These follow the OpenAPI 3.0 Security Scheme format, which allows it to offer broad compatibility.
The underlying philosophy recognizes that different agents will have different security formats and thus different authentication needs. A2A chose flexibility over strict standardization because agent-to-agent communication calls for fundamentally adaptable foundations to cross technical boundaries. Some scenarios need simple API keys, others require full OAuth, and some demand mutual TLS. Enforcing one type of auth would create massive barriers to adoption in heterogeneous systems.
How A2A auth works in practice
The A2A authentication “flow” is pretty straightforward:
The AgentCard declares the required schemes at
/.well-known/agent-card.jsonClient agents discover these requirements via HTTP
GETCredentials are obtained through separate, implementation-specific processes (out of band)
Authentication travels in standard HTTP Authorization headers
Each scheme (Bearer, Basic, ApiKey) follows the OpenAPI 3.0 format
However, unlike authentication, authorization in A2A is left pretty much up to implementers. Remote agents are responsible for access control after authentication, with RBAC (Role-Based Access Control) typically implemented server-side. There’s no standardized authorization model, though the protocol can integrate with existing enterprise IAM (Identity and Access Management) systems.
Key considerations for A2A auth
A2A enables heterogeneous environments to connect, but this increases the implementation burden. Multiple auth methods mean multiple potential attack surfaces. However, for scenarios that call for interoperability, A2A’s open take on auth is essential. Organizations must establish clear trust boundaries and policies underpinning A2A’s limited auth framework rather than relying on it to solve all their integration problems.
A key best practice to remember is standardizing authentication within your organization, even if the A2A protocol doesn’t mandate it.
MCP vs. A2A auth compared
As we established early on, these two protocols serve different purposes and operate at separate layers. While they’re capable of being complementary, tackling auth with one doesn’t mean you’ve solved it for the other. The table below offers a side-by-side comparison of the two approaches and their auth parameters:
MCP | A2A | |
|---|---|---|
Implementation Pattern | Client-to-server | Agent-to-agent |
Auth Standardization | Strict OAuth 2.1 | Flexible, declares multiple schemes via AgentCard |
Discovery Method | ASM, PRM, DCR, CIMD metadata | /.well-known/agent-card.json |
Token Types | OAuth 2.1 access tokens | Bearer, Basic, ApiKey, OAuth, mTLS |
Credential Flows | Authorization code with PKCE | Implementation-specific and out-of-band processes |
Who Manages Credentials | Authorization server | Each implementation determines |
Key Considerations | Enterprise-ready but requires OAuth expertise; spec (both MCP and OAuth 2.1) still evolving | Enables interoperability but increases potential attack surface; warrants internal standardization |
Best practices for deployment
Everyone’s MCP or agent deployment is going to be a bit different depending on organizational needs. However, several security best practices can considerably ease the road to production-readiness.
For MCP
Separate authorization from resource servers (now mandatory in the spec). If you were previously operating under the old spec, it’s time to break those up.
Avoid common MCP server vulnerabilities by staying current with security advisories and only running the most recent version of the specification. Updates aren’t arbitrary; they usually address real concerns.
Monitor and audit all scope requests and token usage. The granularity of OAuth is a huge advantage, but only if you’re actively tracking how it’s being used.
If using DCR instead of CIMD, harden its implementation. Implement the proper safeguards to ensure your client registration process isn’t leaving you open to risk.
Leverage prebuilt solutions and frameworks to reduce dev burden. Time spent engineering and troubleshooting auth is time not invested in your core application. Building OAuth capabilities from scratch (without the necessary expertise) is an invitation for security gaps.
For A2A
Publish clear AgentCards with authentication requirements so client agents can properly prepare before attempting connections.
Establish clear policies for agent-to-agent trust. Just because the protocol is flexible doesn’t mean your security methodology can get away with being poorly defined.
Monitor all inter-agent communications, including token exchange and validation events.
Implement proper authorization, not just for the agents themselves, but also for the resources those agents are accessing.
Deploy fine-grained authorization beyond basic RBAC for enterprise scenarios where it makes sense. Different agents should have different permissions based on their tasks and trust levels.
Remember that A2A auth relies on underlying infrastructure and can’t be a singular security touchpoint. Because of this, it’s critical to ensure that authorization logic (like documents to return) is properly set up.
Consider full OAuth for A2A in enterprise contexts. OAuth offers proven frameworks for AI use cases. Client-Initiated Backchannel Authentication (CIBA), for example, is enterprise-grade, ready-built, and well-suited to agentic scenarios.
Combining both protocols: MCP and A2A auth together
MCP and A2A are far from mutually exclusive. They’re complementary, able to support each other at different but synergistic levels. MCP provides the vertical integration layer (agent-to-tool), and A2A enables the horizontal integration (agent-to-agent).
Workflow example for MCP and A2A auth
To better understand how these protocols’ authentication modalities interact, consider the example of a travel agent system. One agent, the “orchestrator,” uses A2A to delegate tasks to specialized agents, while each of these secondary agents uses MCP to access their respective tools.
Here’s how that might look in practice:
Our flow begins with a prompt from the user to “Book a trip to Tokyo from January 11th to the 18th. Include accommodations, dinner reservations, and activities.”
The orchestrator agent gets to work assigning tasks to its squad of specialized agents
It reads AgentCards to identify the auth methods required for each and obtains the necessary credentials using the out-of-band methods described (Agent A uses OAuth; Agent B uses mTLS; and so on).
Each individual agent might use MCP to access their respective tools or APIs (airline booking, hotel reservation, and ground transportation MCP servers, for example)
Authentication is handled at both layers:
A2A bridges each agent’s framework by communicating and satisfying the individual authentication parameters.
MCP uses OAuth 2.1 for each tool authentication flow
Security considerations when combining protocols
When using MCP and A2A in tandem, it’s important to remember that (while synergistic) these protocols authenticate at different, discrete levels. Just because the authentication for A2A is ironclad, that doesn’t mean the underlying MCP implementation is just as protected. Here are a few security best practices to bear in mind when using these protocols together:
Implement consistent credential management across both protocols to avoid allowing gaps between layers. Cohesion is key, and credentials are powerful regardless of which protocol led to them being obtained.
Use centralized authorization servers whenever possible to maintain a unified security posture. Fragmentation often leads to a splintered view of security, making incidents both more likely and harder to track down.
Ensure audit trails capture activity across both MCP and A2A interactions wherever possible. Equip your deployment with the appropriate data streaming tools to interpret both OAuth events and every type of A2A authentication.
Apply the principle of least privilege and enforce strict, scope-based access at both layers, granting only minimal permissions necessary to perform a specific task.
Securing agentic interactions across every layer
To begin your agentic security implementation, start wherever your use case lives: MCP or A2A, agent-to-tool or agent-to-agent.
To begin, leverage existing auth infrastructure wherever possible rather than building from scratch.
Next, plan for using both protocols to leave room for supplementation, especially in enterprise agent environments where you’ll likely need both vertical and horizontal integration.
Moving forward, stay up to date with MCP and OAuth 2.1 spec changes, which continue to see frequent changes
As your deployment scales and matures, consider auth-as-a-service solutions to speed up production timelines and offload security overhead to proven providers, allowing you to return focus to your core application
By mastering the fundamental differences, considerations, and operational layers of MCP and A2A authentication, you can build better and more secure agentic systems. Even as these protocols continue to evolve, by developing with an eye on the future, you’ll create AI applications ready for production deployment—without worrying about falling behind the security curve.
Securing agents with production-ready, unified auth
Managing authentication across both MCP and A2A layers presents a compound challenge. OAuth flows, DCR/CIMD, scope management, token storage—multiple concerns well outside most organizations’ core competency, and all demanding specialized attention.
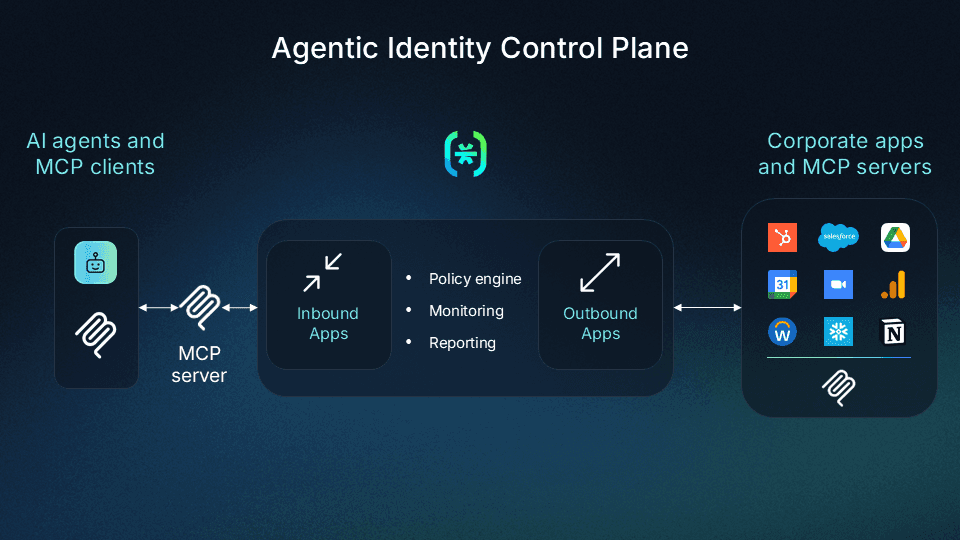
Descope provides comprehensive auth solutions designed specifically for agentic AI / MCP systems.
Teams building external-facing MCP servers can add OAuth 2.1, PKCE, and secure DCR in three lines of code
Teams building AI agents can offload token management and storage for third-party tool connections
Teams building internal-facing MCP servers can implement policy-based AI agent access to corporate tools
Sign up for a Free Forever Descope account to start building enterprise-ready, production-grade auth for your agents, or book a demo with our auth experts to see how Descope can secure your agentic architecture.