Table of Contents
Why modern CIAM is critical for insurance
Quote-to-bind in minutes. Mobile claims. Embedded partnerships. The insurance experience is evolving fast, but identity systems haven’t kept pace. From onboarding friction to unsecured AI agents, the risks are real. Brokers, underwriters, firms, and all stakeholders in the insurance industry need powerful technology to keep up with—and stay ahead of—emerging trends.
In this guide, we explore how customer identity and access management (CIAM) helps insurers solve modern authentication and authorization challenges at scale. Insurance CIAM was built to efficiently handle the specific authorization and authentication challenges in the industry.
Below, we’ll cover:
Why the insurance industry needs CIAM solutions in 2026 and beyond
How insurance CIAM optimizes authentication and authorization functions
How to prepare for AI-based challenges in the insurance industry (and why doing so is necessary)
How to implement and manage an insurance CIAM platform effectively
Why modern CIAM is critical for insurance
Insurance identity and access management is imperative in today’s landscape. It secures customers’ account functions without compromising the smooth experience they expect.
Insurance is no longer bound by in-person agents and lengthy paperwork cycles.
Today’s customers expect instant quotes, mobile self-service, and seamless digital claims. But while the industry is moving fast, many legacy identity systems weren’t designed for this shift. They lack modern user experience (UX), strong but nimble access controls, and the flexibility to scale across complex B2B2C ecosystems.
Outdated login flows and siloed data systems create friction and vulnerability. According to Gartner, a whopping 93% of insurance leaders now cite customer experience (CX) as a top priority for 2025. Yet, weak authentication flows and poor password hygiene continue to erode trust and conversion.
Modern insurance CIAM addresses this by enabling fast and secure onboarding and account access. For example, customers can register with a passkey or one-time password (OTP) instead of a password, reducing friction and improving security. And IT teams can benefit from centralized policy enforcement, streamlined SSO for agents and partners, and built-in multi-factor authentication (MFA) across all user types.
CIAM for insurers also helps meet evolving regulatory requirements:
NYDFS Section 500.12b mandates MFA for privileged access.
EU-based insurers must meet DORA’s resilience standards.
U.S. health insurers must maintain HIPAA compliance.
These standards require specific security safeguards, like fine-grained access controls and audit-ready identity logs. But without careful implementation, these controls can sometimes create bottlenecks and other frictions that negatively impact customers.
Additionally, insurers don’t just manage policyholders—they also serve agents, brokers, MGAs, embedded partners, and other third-party stakeholders. That’s a lot of different user types, each needing the right level of access to the right systems at the right time. Insurance CIAM makes it easy to support these B2B2C relationships without creating silos or sacrificing security.
At the end of the day, CIAM helps insurers improve experiences while staying secure and adaptable as business demands evolve.
Read more: IAM vs. CIAM Explained & How to Choose
Authentication in the insurance context
Insurance CIAM centers around two core concepts: authentication and authorization. The former, authentication, is the foundation of CIAM. It’s the process of ensuring that users are who they claim to be. In the insurance world, this includes policyholders, agents, brokers, internal administrators, and other stakeholders who access sensitive data or systems.
Authentication begins at account creation, but it plays a critical role during every login session, interaction with claims, and account update throughout the user lifecycle.
Key best practices include:
Multi-factor authentication (MFA)
MFA is a baseline requirement in regulated industries like insurance, but not all MFA is created equal. Traditional MFA approaches, like always requiring an SMS OTP, can frustrate users. They are also increasingly vulnerable to phishing and SIM-swap attacks.
Adaptive MFA, on the other hand, uses contextual risk signals such as IP reputation, geolocation, device fingerprinting, and session anomalies to apply just the right level of friction. For example, a broker accessing a client portal from a known device may need only a biometric confirmation, while an unrecognized login from another country might trigger step-up authentication. This way, security assurance is balanced with a positive, welcoming UX.

Adaptive MFA via insurance CIAM helps firms remain compliant with frameworks like NYDFS and HIPAA. These and other rulesets require MFA or equivalent protections, and regulators are increasingly adding to MFA requirements to include adaptive qualities for phishing-resistance.
For high-risk actions, step-up authentication adds an extra layer of assurance. Updating a beneficiary, submitting a claim, or accessing financial payout data might require a stronger form of identity proofing, such as a biometric check or reauthentication.
Passwordless authentication
Passwords remain a leading cause of breaches and support overhead. In insurance, where users span consumers, agents, and field staff, passwordless methods help reduce cognitive load and security risk.
Two commonly used passwordless methods are passkeys and magic links.
Passkeys, based on public-private key pairs stored securely on a user’s device, are phishing-resistant and supported across platforms through standards like WebAuthn. They’re especially effective for insurance customers accessing portals via mobile, offering a secure and seamless login experience without the need for usernames or passwords.
Magic links, while simpler to implement and more familiar to users, rely on time-bound, single-use tokens sent via email or SMS. When implemented properly—with short expiration windows and protections against token replay—they provide a frictionless alternative to passwords, particularly for infrequent users or one-time access scenarios.
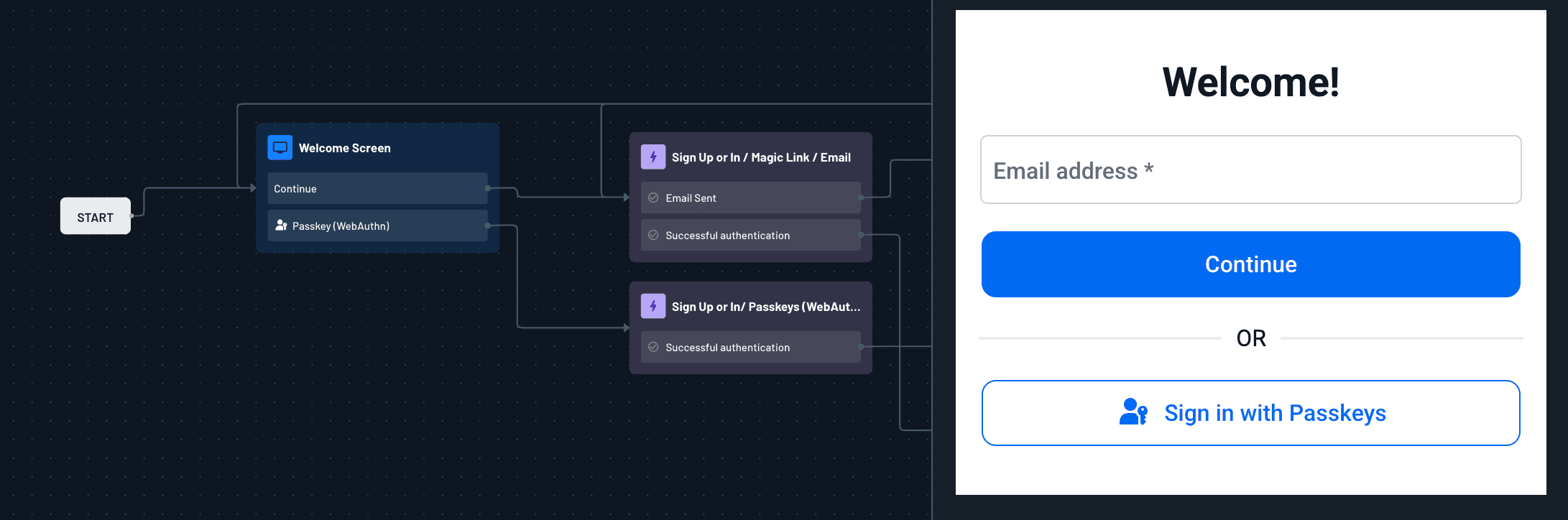
These methods improve security posture while eliminating the need for users to remember complex passwords—or worse, reuse weak ones.
Federated login and Single Sign-On (SSO)
In insurance, users rarely operate within a single system or organization. Policyholders, agents, brokers, MGAs, and embedded partners often need access across multi-party ecosystems with multiple portals or platforms—many of which are managed by different entities.
This is where federated authentication and single sign-on (SSO) come in.
Federated authentication allows users to log in once using credentials from a trusted third party, like a broker’s corporate login or a customer’s personal account, and gain access to external systems without needing to create and manage new credentials. This makes access faster, more secure, and far less prone to credential reuse or mismanagement.
SSO, by comparison, is typically used within a single organization to help users move between related systems, such as claims, quoting, and CRM tools, without logging in again each time.
Both approaches reduce friction and improve security, but in a multi-entity ecosystem like insurance, federated authentication is especially critical. It enables seamless collaboration between external stakeholders without compromising control or user experience.
Federated logins and SSO are key parts of insurance CIAM’s scalability.
Identity verification (IDV)
For high-risk operations like onboarding, claims disbursement, or beneficiary updates, verifying user identity goes beyond login credentials. These situations require identity verification (IDV).
In the context of insurance CIAM, IDV helps satisfy Know Your Customer (KYC) and Anti-Money Laundering (AML) requirements, reduces synthetic identity fraud, and supports compliance with regulations. IDV should also be repeatable across the customer lifecycle, not just at onboarding.
Insurance carriers should integrate modern IDV methods, like document scanning (OCR and liveness checks), government database validation, and biometric match-on-photo.
Also read: Frictionless IDV with Incode and Descope
Authorization: Managing identity in a complex insurance ecosystem
If authentication is about confirming who someone is, authorization is about defining what they can do: what systems or data they can access, under what conditions, and for how long.
In insurance, this becomes especially complex.
Carriers must manage identity and access for not just employees, but also policyholders, brokers, assistants, partner firms, and, in some cases, family members acting on someone else’s behalf. Without the right access controls, it’s easy to over-provision permissions, expose sensitive data, or create friction that slows down service delivery.
To avoid these pitfalls, modern CIAM in insurance should rely on access control models like:
Role-based access control (RBAC) – Grants access based on predefined roles like "policyholder," "agent," or "claims adjuster." RBAC is simple to implement, but can become rigid as relationships grow more complex.
Attribute-based access control (ABAC) – Builds access rules based on user attributes, such as policy type, geographic region, or license level. ABAC allows for finer-grained control in high-variability environments.
Relationship-based access control (ReBAC) – Adds an additional layer of context by tying access to specific relationships (e.g., “parent of minor,” “broker for client X”). This is especially useful in multi-party insurance scenarios and embedded offerings.
These models help limit over-provisioning and support regulatory compliance by ensuring users only access what they need—nothing more, nothing less.
Equally important is scoped access and delegation. Insurance often involves people acting on behalf of others: parents managing children’s coverage, executive assistants handling group policies, or caregivers accessing medical claim details. CIAM should support secure, auditable delegation flows that allow access to be granted with clearly defined permissions and expiry conditions.
On the organizational side, self-service identity administration is key to scaling securely. Brokers and partner firms should be empowered to manage their own teams, invite new users, and handle basic account admin without needing to go through a carrier’s IT department for every update. This keeps operations agile while maintaining control through centralized policies and audit logs.
Robust authorization practices don’t just reduce risk, they make it easier to deliver seamless, compliant service at scale. In the insurance ecosystem, it’s not a nice-to-have; it’s essential.
Preparing for AI-driven challenges
As generative AI becomes an integral part of insurance operations, traditional approaches to identity and access management are being reevaluated in new ways. Per Gartner, 90% of insurance organizations plan to increase GenAI funding in 2025, fueling the rise of internal copilots, customer-facing chatbots, and backend automation agents. AI tools offer major efficiency gains, but they also introduce serious access and accountability challenges.
This is why a CIAM platform custom-built for insurance use cases is especially important.
Most CIAM frameworks were built to manage human users and applications, not autonomous agents acting on someone’s behalf. Insurance CIAM platforms need to account for risks like:
Unsecured API access by AI agents – Many AI tools access internal systems via APIs, often using shared credentials or hardcoded tokens. Without secure token handling and identity verification, it’s difficult to trace or limit what these agents are doing.
Lack of scoped permissions or audit trails – Once an AI agent is granted access, there's often little visibility into its actions, or easy ways to revoke or adjust that access. This creates blind spots that can undermine security, compliance, and trust.
Shadow AI misuse – Employees may use personal or unauthorized AI tools to automate tasks or handle customer data. This “shadow AI” can unintentionally expose sensitive policyholder information, putting the organization at risk.
To address and mitigate these risks (and thereby minimize potential harm), insurance CIAM systems must evolve to treat AI agents as first-class actors in the broader identity fabric. That includes:
Using secure authorization protocols (like OAuth 2.0) to manage agent access via scoped tokens tied to specific systems and users
Applying granular authorization policies to define exactly what actions an AI agent can perform, such as retrieving a quote but not binding a policy
Implementing robust token lifecycle management, including expiration, refresh, and revocation mechanisms for external-facing tools
Logging and monitoring AI activity just as you would for human users, ensuring traceability and accountability across every interaction
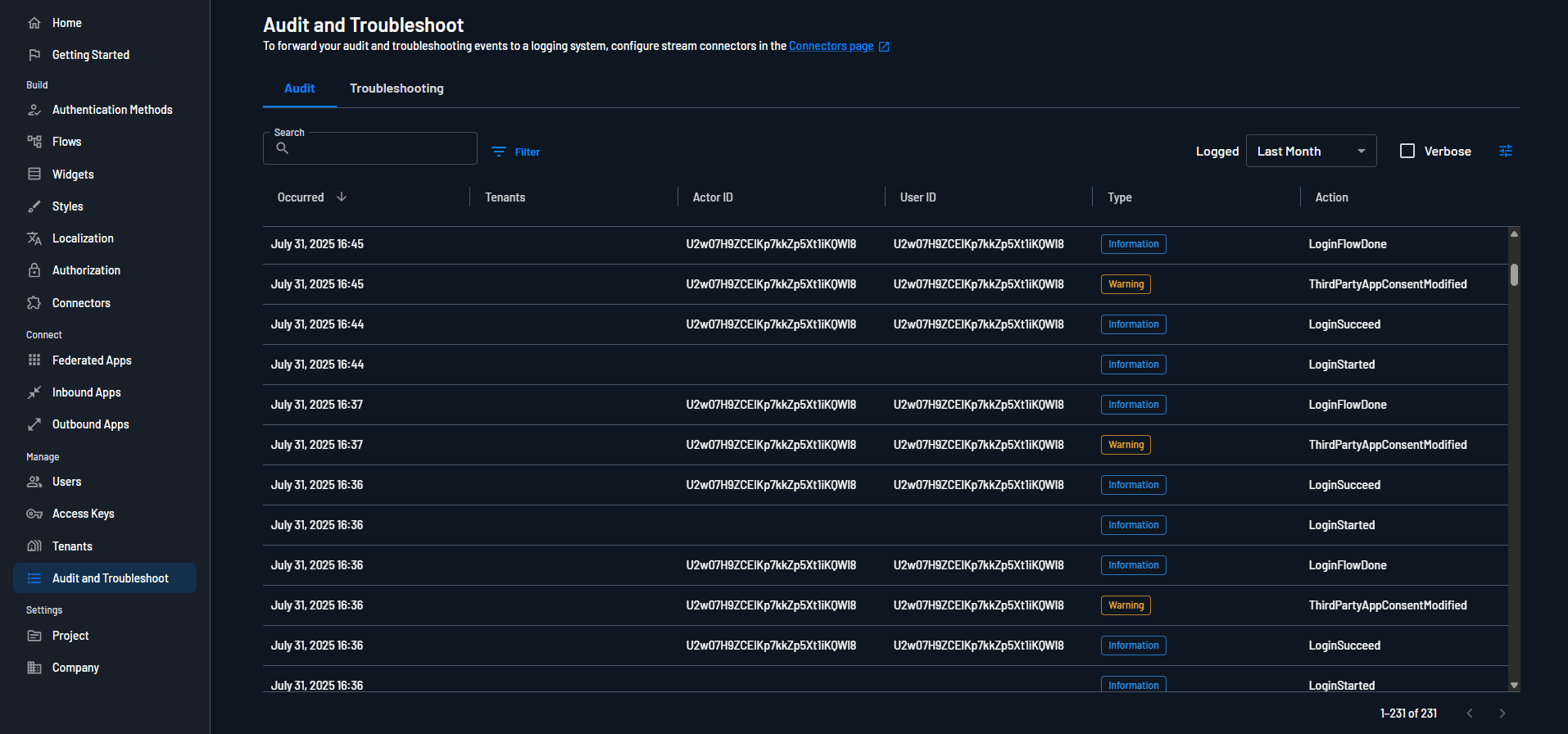
As AI becomes embedded in claims workflows, quoting engines, and policy servicing, identity systems need to keep pace. Insurance CIAM must extend beyond people and apps to top-down governance to control the growing class of autonomous agents operating in between.
Read more: Securing APIs With Progressive Scoping
Insurance CIAM implementation considerations and best practices
Designing and deploying CIAM for insurance isn’t just a technical exercise; it’s a balancing act between security, usability, scalability, and compliance. The best systems empower users while reducing risk, not by locking down access, but by making it intelligent and contextual.
Balance security with user experience
Customers shouldn’t have to jump through hoops just to get a quote. Repetitive MFA prompts, clunky login flows, or overreaching consent gates can drive drop-off and reduce satisfaction. Adaptive authentication should step in only when risk signals warrant it, not as a default.
Design for flexibility and scale
Modern insurance ecosystems rely on a growing number of external actors. CIAM platforms should support multiple identity providers (IdPs) on the broker side and enable multi-tenancy to isolate partner access while efficiently using shared infrastructure.
Streamline operations with self-service and no-code tools
Insurance CIAM should reduce the burden on IT, not add to it. Features like embedded login, self-service portals, and delegated user management help resolve access issues without tickets or manual intervention. No-code workflows make it easier to roll out changes, enforce policies, and respond to emerging threats without engineering bottlenecks.
Meet compliance and audit expectations by design
CIAM must log all identity events for auditability and enforce data privacy policies aligned with frameworks like HIPAA, GLBA, and other regional regulations. This includes granular consent management, retention policies, and role-based access rules.
Build on a future-ready identity architecture
CIAM should be mobile-first, with consistent authentication across native apps and web interfaces. They should support OAuth-based API protection for services and external AI agents, and apply fine-grained authorization to control how large language models (LLMs), copilots, or automation agents interact with customer data.
Read more: The Developer's Guide to AI Chatbot Authorization
Ultimately, successful insurance CIAM implementation isn’t just about checking boxes. It’s about giving insurers the tools to scale securely, serve faster, and stay ahead of the next generation of digital and AI-driven risk.
CIAM that works the way modern insurance does
Today’s insurance platforms must support fast quotes, frictionless onboarding, secure delegation, and complex partner ecosystems. Descope is a CIAM platform purpose-built for insurance companies to make this happen.
From passkey-based login and adaptive MFA to embedded flows, delegated access, and broker-ready SSO, Descope gives you everything you need to simplify identity without compromising security. You can even track anonymous users, manage AI agent access, and enable multi-tenant separation—all with no-code workflows and developer-first tooling. Case in point: Branch Insurance augmented their existing auth systems with Descope passkeys, resulting in a 50% drop in auth-related support tickets.
Get started with a Free Forever Descope account, or book a demo to see how we can support your CIAM strategy.






